|
This chapter describes how to use CommView for WiFi to connect
to CommView Remote Agent for WiFi and capture traffic remotely. To
monitor wireless network traffic using remote computers, you need
to have CommView Remote Agent for WiFi running on the remote host
and CommView for WiFi running on your computer. It is assumed that
Remote Agent is already installed and running (see the previous
chapter for instructions) and that you are already familiar with
CommView for WiFi and know how to use it. If you have no experience
with CommView for WiFi, please download it and familiarize yourself with it
prior to using CommView Remote Agent for WiFi.
Using CommView
for WiFi to Connect to CommView Remote Agent for WiFi
To switch to remote monitoring mode, click File => Remote Monitoring Mode. An additional
toolbar will appear in the CommView for WiFi main window next to
the main toolbar. If you are behind a firewall or proxy server, or
using a non-standard Remote Agent port, you may need to click on
the Advanced Network Settings button to change the
port number and/or enter SOCKS5 proxy server settings. The
Advanced Network Settings dialog also allows you
to define whether Remote Agent will apply the filtering rules
locally, or send all the captured traffic to CommView for WiFi;
this will be discussed in detail later in this chapter.
Click on the New Remote Agent
Connection button to establish a new connection, or click on
the Load Remote Agent
Profile toolbar button to load a previously saved Remote
Agent connection profile. A previously saved profile may also be
loaded from the New Remote Agent Connection window.
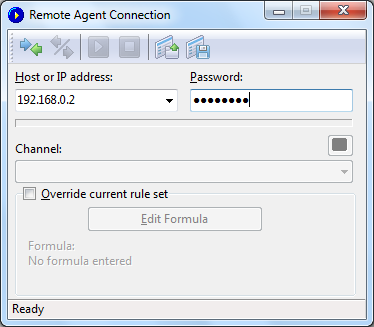
A Remote Agent Connection window will appear. Enter the IP
address of the computer running CommView Remote Agent for WiFi into
the IP address input area, enter the connection password and click
on the Connect button. If
the password is correct, a connection will be established. You will
then see the Link Ready
message in the status bar and the channel selection box will
list the channels supported by the wireless adapter installed on
the remote computer. In addition to the channel list, a special
Scanner Mode item will be
added as the first item on the list.
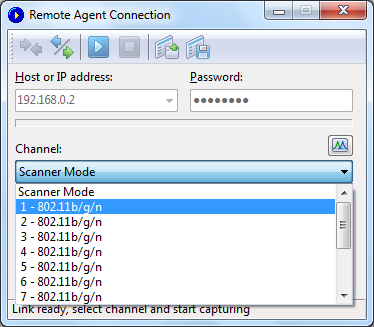
If you select Scanner
Mode, the remote wireless adapter will cycle through the
available channels, capturing data from each of them for several
seconds. The small button located on the right side of the window,
just above the channel selection box, allows you to adjust the
scanner settings. Click on this button to select the channels to be
monitored in Scanner Mode and set the interval, i.e. the number of
seconds per channel. Note that for Intel wireless adapters, the
interval cannot be below 4 seconds due to technical
limitations.
Now is the best time to configure the capturing rules using the
Rules tab in the CommView
for WiFi main window. You can also apply a custom set of capturing
rules to this connection and override the current rules defined in
CommView by checking the Override
current rule set box, clicking on the Edit Formula button and entering the
rules formula in the field below. The formula syntax is the same as
the one used in Advanced Rules. Once you're ready to start
monitoring, select the channel from the list and click the
Start Capture toolbar button. CommView for
WiFi allows you to save the Remote Agent Connection settings as a
connection profile for quick and easy access in the future. Click
on the Save Remote Agent
profile toolbar button in the New Remote Agent Connection
window and enter a name for the file.
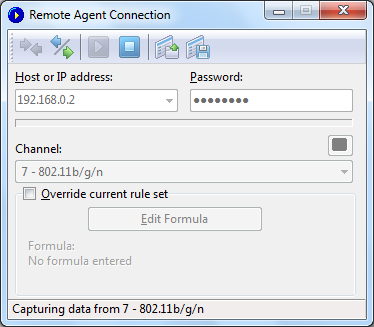
CommView for WiFi will start to capture the remote adapter's
traffic as if it's your local network traffic; there is virtually
no difference between using CommView for WiFi locally or remotely.
When you are done with remote monitoring, just click on the
Stop Capture toolbar
button. You can then change the channel or disconnect from Remote
Agent by clicking the Disconnect toolbar button. To return to
the standard mode, click File => Remote Monitoring Mode, and the
additional toolbar will disappear.
Please note that CommView for WiFi can work with multiple Remote
Agents simultaneously. You can open several remote connections,
each having its own settings and an independent set of rules and
collect the traffic from remote WLANs in one CommView for WiFi
instance.
How to Use
CommView Remote Agent for WiFi Efficiently
The key to efficient Remote Agent usage is ensuring that enough
bandwidth is available to transfer the data collected by Remote
Agent to CommView for WiFi. As mentioned before, Remote Agent
should be installed on a computer that has a compatible wireless
adapter (to be used for monitoring) and Ethernet adapter (to be
used for the connection between Remote Agent and CommView for
WiFi).
By default, Remote Agent sends all the collected packets back to
CommView for WiFi, regardless of the capturing rules that may be
configured in CommView for WiFi. This is done for providing correct
statistical data and decryption, as well as the means for correct
identification of wireless nodes. Since a fully loaded WiFi network
has a bandwidth of 54 Mbit/ss (or even 300 Mbit/s with newer
802.11n hardware), it's important that the wired link between
Remote Agent and CommView for WiFi be capable of handling this
bandwidth. In a modern office environment, where Gigabit networks
are common, a single Gigabit adapter can easily receive data from a
dozen Remote Agents.
There are situations where a fast connection is problematic. For
example, a high bandwidth connection may not be available if you're
monitoring a remote WLAN over the Internet. Even a T3 connection
(4.5 Mbit/s) is insufficient to transfer all packets from a
moderately loaded WLAN. In such situations, you can change the
default setting and make Remote Agent filter the packets before
they are transferred to CommView for WiFi. The Advanced Network Settings button on the
additional remote monitoring toolbar in the main CommView for WiFi
window allows you to enable the Minimize bandwidth option. When this
option is enabled, the current CommView for WiFi rule set is
periodically sent to Remote Agent. This rule set is then applied
locally, so that only those packets that pass the rules are sent
back to CommView for WiFi. In this mode, the Nodes may not display any nodes, and
the Channels tab will not
show full per-channel statistics, so use this mode only when you
have limited bandwidth, but still need access to the packets
from a remote WLAN.
For the same bandwidth reasons, it is highly recommended to NOT
use a wireless connection for exchanging data between Remote Agent
and CommView for WiFi. It's also a bad idea because the monitoring
wireless adapter would pick up the packets sent by the wireless
adapter being used for communicating with CommView for WiFi if they
operate on the same or close channels. This will simply cause the
snowball effect.
If CommView Remote Agent for WiFi captures more data than it can
send to CommView for WiFi, it uses an internal buffer to store the
packets that cannot be sent immediately. The buffer size is 5
Mbytes. The Buffer
utilization indicator in the Remote Agent window shows the
current status of the buffer. For example, if the program has
buffered 2.5 Mbytes of data, the buffer utilization is 50%. If/when
the buffer utilization reaches 100%, the program stops buffering
data and discards captured packets until some buffer space is
free.
Security
CommView Remote Agent for WiFi was made with security in mind.
It can be accessed only by using a password that is never
transmitted in plain text and that is ensured by using a
challenge-response protocol with a secure hash function. If the
authentication is successful, all transmitted traffic is compressed
and then encrypted with the same password. Please take precautions
to keep your password secret. Once it is revealed to an
unauthorized person, that person will have broad capabilities to
study your network and intercept network traffic on the remote
computer.
|

