Using the Program
Driver Installation
CommView for WiFi is a tool for monitoring wireless 802.11 a/b/g/n/ac/ax networks. You must have a compatible wireless adapter to use this product. In order to enable the monitoring features of your wireless adapter, you will need to use the special drivers that come with this product. When CommView for WiFi is not running, your adapter will be able to connect and communicate with other wireless hosts or access points, as it normally does. When CommView for WiFi is running, your adapter will be put in passive, promiscuous monitoring mode with no connectivity.
Prior to installing the new driver for your wireless adapter, be sure that your adapter is compatible with this product. The list of compatible adapters can be found at the following URL:
https://www.tamos.com/products/commwifi/.
CommView for WiFi may support other adapters. If your adapter is not listed above, please refer to the FAQ chapter for up-to-date information.
For detailed, illustrated driver installation instructions, please launch the program, click Help => Driver Installation Guide in the program's menu, and scroll down to the bottom of the window.
Overview
The program interface consists of several tabs that allow you to view data and perform various actions with captured packets. The functionality of these tabs is described in the table below.
| Tab Name | Description |
| Nodes | Controls packet capture, displays detailed information on access points and associated stations, channel utilization statistics, and graphical representation of the wireless spectrum. |
| Channels | Displays detailed per-channel statistics, as well as the top nodes, Mbytes per second, and packets per second charts. |
| Latest IP Connections | Displays detailed information on the latest IP connections between the WLAN nodes. This information is available when the WLAN being monitored does not use encryption or when you have entered the correct WPA or WEP key. |
| Packets | Lists captured packets; allows you to examine them and view their contents. |
| VoIP | Provides in-depth VoIP analysis of the captured traffic. Note that this tab is only available to VoIP license users or evaluation version users who selected VoIP evaluation mode. |
| Logging | Allows you to save captured packets to log files in a number of formats and configure automatic logging. |
| Rules | Provides access to packet filters that allow you to capture/ignore packets based on various criteria, such as IP address or port number. |
| Alarms | Allows you to create alarms that can notify you about important events, such as suspicious packets, high bandwidth utilization, unknown addresses, etc. |
You can change some of the settings, such as fonts, colors, and buffer size by selecting Settings from the menu. For more information, see Setting Options.
Main Menu
The application menu commands are described below.
File
- Start/Stop Capture – starts/stops capturing packets.
- Suspend/Resume Packet Output – stops/resumes the real-time packet output on the Packets tab.
- Remote Monitoring Mode – shows or hides the remote monitoring toolbar that allows you to connect to remote capture devices: Remote Agent for WiFi, RPCAP, or Aruba Remote Capture.
- Save Nodes As – allows you to save the contents of the Nodes tab.
- Save Channels As – allows you to save the contents of the Channels tab.
- Save Latest IP Connections As – allows you to save the contents of the Latest IP Connections tab.
- Save Packet Log As – allows you to save the contents of the Packets tab in different formats. Use the Logging tab for advanced saving options.
- Log Viewer – opens a new Log Viewer window.
- VoIP Log Viewer – opens a new VoIP Log Viewer window.
- Clear Nodes – clears the Nodes tab.
- Clear Channels – clears the Channels tab.
- Clear Latest IP Connections – clears the Latest IP Connections tab.
- Clear Packet Buffer – clears the contents of the program's buffer and the Packets tab.
- Clear VoIP Data – clears the contents of the VoIP tab.
- Performance Data – displays the program's performance statistics: the number of packets captured and dropped by the device driver.
- Exit – closes the program.
Search
- Find Packet – shows a dialog that allows you to find packets matching a specific text.
- Go to Packet Number - shows a dialog that allows you to jump to a packet with the specified number.
View
- Statistics – shows a window with data transfer and protocol distribution statistics.
- Port Reference – shows a window with port reference information.
- Log Directory – opens the directory to which logs are saved by default.
- Nodes Columns – shows/hides the Nodes tab columns.
- Channels Columns – shows/hides the Channels tab columns.
- Latest IP Connections Columns – shows/hides the Latest IP Connections tab columns.
- Packets Columns – shows/hides the Packets tab columns.
- Channels and Spectrum – shows/hides the Channels and Spectrum pane at the bottom of the Nodes tab.
Tools
- Packet Generator – opens the Packet Generator window.
- Reconstruct TCP Session – allows you to reconstruct a TCP session starting from the selected packet; it opens a window that displays the entire conversation between two hosts.
- Reconstruct UDP Stream – allows you to reconstruct a UDP stream starting from the selected packet; it opens a window that displays the entire conversation between two hosts.
- NIC Vendor Identifier – opens a window where you can identify a network adapter vendor by MAC address.
- Scheduler – allows you to add or remove scheduled capturing tasks.
- Node Reassociation – opens the Node Reassociation window.
Settings
- Fonts – shows the submenu for setting the fonts of the interface elements.
- WEP/WPA Keys – opens a window that allows you to enter WEP/WPA keys.
- MAC Aliases – brings up a window where you can assign easy-to-remember aliases to MAC addresses.
- IP Aliases – brings up a window where you can assign easy-to-remember aliases to IP addresses.
- Options – brings up the Options window where additional advanced program options can be set.
- Language – allows you to change the interface language. Be sure to restart the program once you have changed the language. The CommView for WiFi installation package may not include all available language files for the interface. Clicking on the Other Languages menu item opens the additional languages download page on our Website where you can download your language file if it is available for the current version.
Rules
- Capture Data Packets – check or uncheck this item to enable/disable capturing of packets of the type "Data".
- Capture Management Packets – check or uncheck this item to enable/disable capturing of packets of the type "Management".
- Capture Control Packets – check or uncheck this item to enable/disable capturing of packets of the type "Control".
- Ignore Beacons - check or uncheck this item to enable/disable capturing of management packets of the type "Beacon".
- Save Current Rules As – allows you to save current rules configuration to a file.
- Load Rules From – allows you to load a previously saved rules configuration from a file.
- Reset All – clears all existing rules (if any).
Help
- Contents – launches CommView for WiFi help.
- Search For Help On… – shows CommView for WiFi help index.
- Driver Installation Guide… – shows detailed driver installation instructions.
- Check for an Update on the Web – opens the update wizard. Please follow the instructions on the screen to download and install the latest upgrade for CommView for WiFi from the TamoSoft website.
- Activation – allows you to activate your software license or check the current activation status.
- About – shows information about the program.
Nodes
This is the main application tab that is used for controlling packet capture, displaying detailed information on access points and associated stations, channel utilization statistics, and graphical representation of the wireless spectrum.
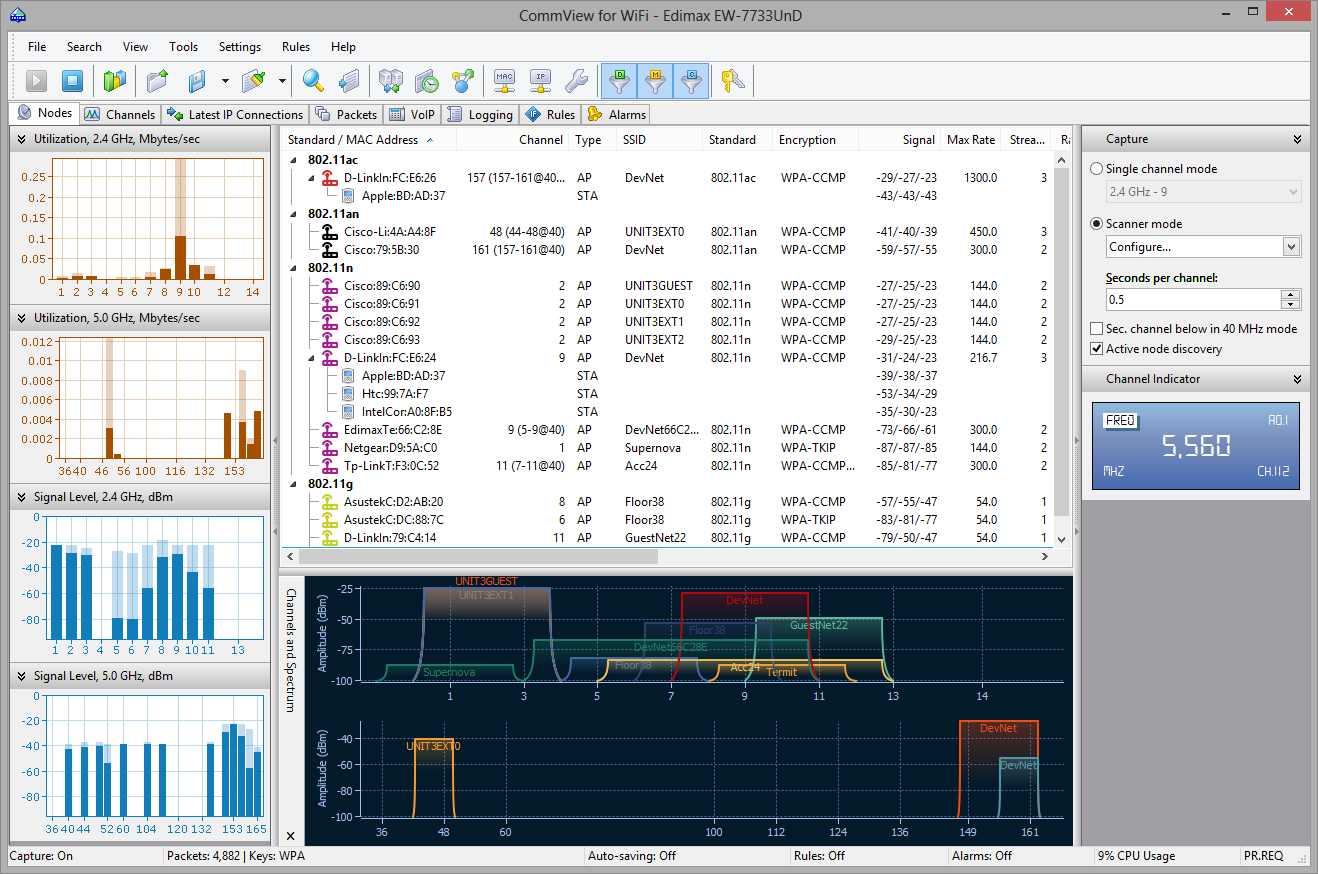
This window consists of several resizable panes that are overviewed below.
Capture and Channel Indicator Panes
This Capture pane allows you to choose between the two capturing modes: Single channel mode or Scanner mode. If you select the Single channel mode, the application captures packets on a single channel (or several channels, if you use several supported USB cards; more information is given below) that you can select from the drop-down list. If you select the Scanner mode, the application will sweep through the channels in a loop, i.e. it will capture on the first channel, switch to the next channel thereafter, and so forth, until it reaches the last channel, after which a new scanning cycle will begin. To configure the set of channels to be scanned, click Configure and use the checkboxes to select or unselect specific channels. Depending on the country and regulatory domain set in your adapter, the list of supported channels may vary. This is discussed in the FAQ chapter in detail. To configure the time the application spends on each channel, use the Seconds per channel edit box.
You can also see two other options at the bottom of this pane that control packet capture. The Sec. channel below in 40 MHz mode check box determines the position of the secondary channel when channel bonding is used in the 2.4 GHz band. By default, the secondary channel in 40 MHz 802.11 networks has a higher frequency than the primary channel. If you are capturing packets in a network environment that has a lower frequency secondary channel, check this box. Checking this box has no effect if the secondary channel cannot be positioned below the primary one, which is the case when, for example, you are capturing on 2.4 GHz channel 1, 2, 3, or 4. This option is available only if your adapter supports capturing on 40 MHz channels. The Active node discovery box makes the application send PROBE REQUEST packets periodically. Such packets facilitate the discovery of those APs that do not broadcast their SSID. This option is available only if your adapter supports packet generation.
Once you have configured the capture options, click the Start Capture button on the toolbar. If you want to switch to a new channel while you are in the Single channel mode or switch to the Scanner mode, you can do so without stopping capturing. The Channel Indicator pane displays the current channel and frequency while the application is capturing packets.
Using Multiple Adapters for Multi-Channel Capturing
If you need to capture packets on multiple channels simultaneously, you can do so by using multiple USB adapters. In this mode, the channel selection drop-down list becomes a multi-select control that allows you to select several channels by holding down the Ctrl key. The Channel Indicator pane will then display several channel/frequency indicators. Note that using multiple adapters is supported only for a limited set of adapter models. Please refer to the Multi-channel Capturing chapter for the detailed information.
Node List
Once you have started capturing, the program begins to populate the node list with detected wireless nodes. The packet analysis mechanism used in the program lists all the access points found on the given channel(s) and stations in ad hoc mode, as well as associated stations in infrastructure mode. It is important to understand that the radio used in a wireless adapter can receive data on only one channel at a time. Therefore, when you have selected a certain channel for monitoring, this table will contain data on the APs and stations transmitting data on the selected channel only. You can, however, select a different channel without resetting data in the table or select the Scanner mode to make the application sweep through the channels so that you can see active nodes on different channels.
The meaning of the table columns is explained below:
- SSID/Band/Channel – depending on the grouping method that you selected (accessible via the Group by context menu), the first column lists wireless nodes grouped by SSID, 802.11 standard, or channel. Each wireless node is represented by its MAC addresses or alias. The stations associated to APs are shown as "child" items linked to the "parent" item representing the AP.
- Channel – the channel the given AP works on. If the AP uses channel bonding (40, 80, or 160 MHz channels), the primary channel is listed first, followed by information on the additional channels in parentheses.
- Type – node type. Possible values are AP (for access points), STA (for stations in infrastructure mode) and AD HOC (for stations in ad hoc mode).
- SSID – Service Set Identifier; a unique string that differentiates one WLAN from another.
- Standard – 802.11 standard of the AP. Possible values are 802.11a, 802.11b, 802.11g, 802.11n, 802.11an, and 802.11ac.
- Encryption – shows whether the node is using WEP or WPA encryption. For access points, this column shows available encryption methods being "advertised" by the access point.
- Signal – signal level in the min/average/max format. The average value is calculated since the data in this table was last reset. Please refer to the Understanding Signal Strength chapter for more information.
- Max Rate – the maximum PHY data rate the AP can provide.
- Streams – the number of spatial streams supported by the AP.
- Rate (Tx and Rx) – data transfer rate in the min/average/max format. The average value is calculated since the data in this table was last reset.
- Bytes (Tx and Rx) – the number of bytes sent and received by the node.
- Packets (Tx and Rx) – the number of packets sent and received by the node.
- Retry (Tx and Rx) – the number of packets where the Retry flag was set.
- Fragmented (Tx and Rx) – the number of packets where the Fragmented flag was set.
You can show or hide individual columns by right-clicking on list header or using the View => Nodes Columns menu. The column order can be changed by dragging the column header to a new location. Right-clicking on the node list brings up a menu with the following commands:
- Details – displays an AP and Station Details window.
- Quick Filter – finds the packets sent to/from the selected node, as well as the packets where the MAC address of the selected node equals the BSSID address, and displays them in a new window.
- Copy MAC Address – copies the selected node MAC address to the clipboard.
- Create Alias – displays a window where you can assign an easy-to-remember alias to the selected MAC address.
- Save Nodes As – allows you to save the contents of the Nodes tab as an HTML report.
- Clear Nodes – clears the table.
- More Statistics – shows a window with data transfer and protocol distribution statistics.
- Group by – groups the list by SSID, channel, or band.
Utilization and Signal Level Panes
Located on the left side of the Nodes tab, these panes display per-channel utilization charts (two separate charts for 2.4 GHz and 5 GHz channels) and per-channel signal level charts (again, two separate charts for 2.4 GHz and 5 GHz channels). In addition to the current levels, these charts also display historic high levels, which are illustrated in a pale color.
Channels and Spectrum Pane
Located at the bottom of the Nodes tab, this pane has dual functionality:
- It provides a graphical representation of the active APs, where each AP is shown using a line that approximates its spectrum mask. The mask width depends on the channel width supported by the AP and the mask height depends on the current signal strength.
- It can display spectrum data if you plug in a USB-based spectrum analyzer, WiPry by Oscium or Wi-Spy by MetaGeek. A spectrum analyzer listens to and analyzes the frequency bands utilized by Wi-Fi devices. Because these bands are unlicensed, they are often shared with non-Wi-Fi sources of RF signals, such as wireless video cameras, microwave ovens, or cordless phones, which cause interference. The purpose of spectrum analysis is to detect and identify such sources of interference, eliminate them, and/or identify the WLAN channels with minimal interference. For more information, please refer to the Spectrum Analysis chapter.
AP and Station Details Window
When you double-click on an AP or a station shown on the Nodes tab, CommView for WiFi displays a window that contains detailed data on the selected node, as illustrated below.
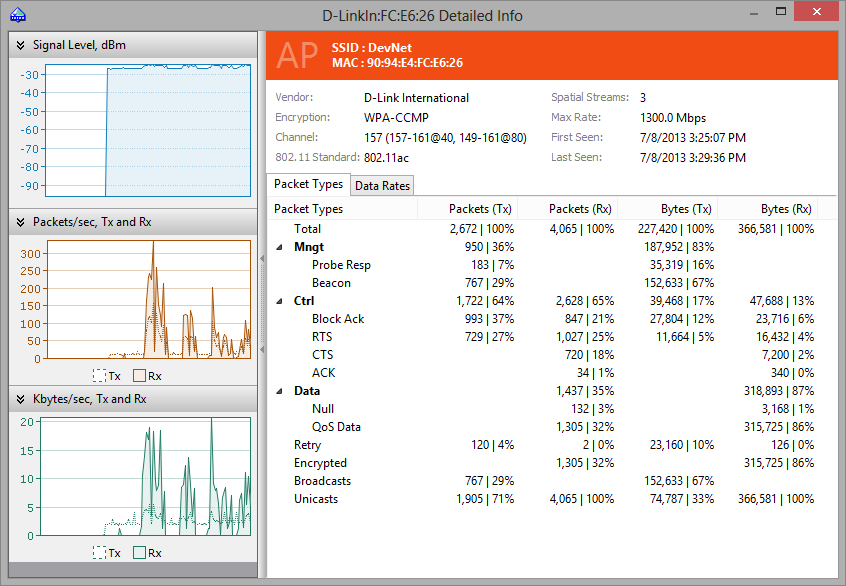
The top pane displays the type, MAC address, and SSID of the selected node, followed by other key details, such as channel, first seen and last seen times, etc. This pane uses the same color that is used to display the selected AP on the Channels and Spectrum pane of the main application window.
On the bottom pane, you can see Packet Types and Data Rates tables. These tables display detailed statistics for the selected channel based on the packet types and subtypes and on the data rates.
On the left pane, you can see three charts: Signal Level, Packets/sec, and Mbytes/sec. The Signal Level chart displays the signal level for the given node. The Packets/sec and Mbytes/sec charts show the number of packets and Mbytes per second sent to/from the given node. Note that these charts are updated only when the application actually captures data on the channel on which the given node is working. This means that if, for example, you are capturing data on channel 5 and the selected AP is also working on channel 5, then the charts will be constantly updated. However, if you are using the Scanner Mode, the charts will be updated every time the application sweeps through the channel on which the given AP is working.
Channels
This tab displays per-channel statistics for all the channels that have been or are being monitored. The number of channels shown in this table depends on the way you use CommView for WiFi. Normally, when you monitor only one channel used by your WLAN, the table will solely contain data on the selected channel, because the radio used in a wireless adapter can receive data on only one channel at a time. Once you have selected a different channel for monitoring, another channel will be added to the table. If you select the Scanner mode on the Nodes tab, the table will contain data on all the scanned channels for which at least one packet has been captured.
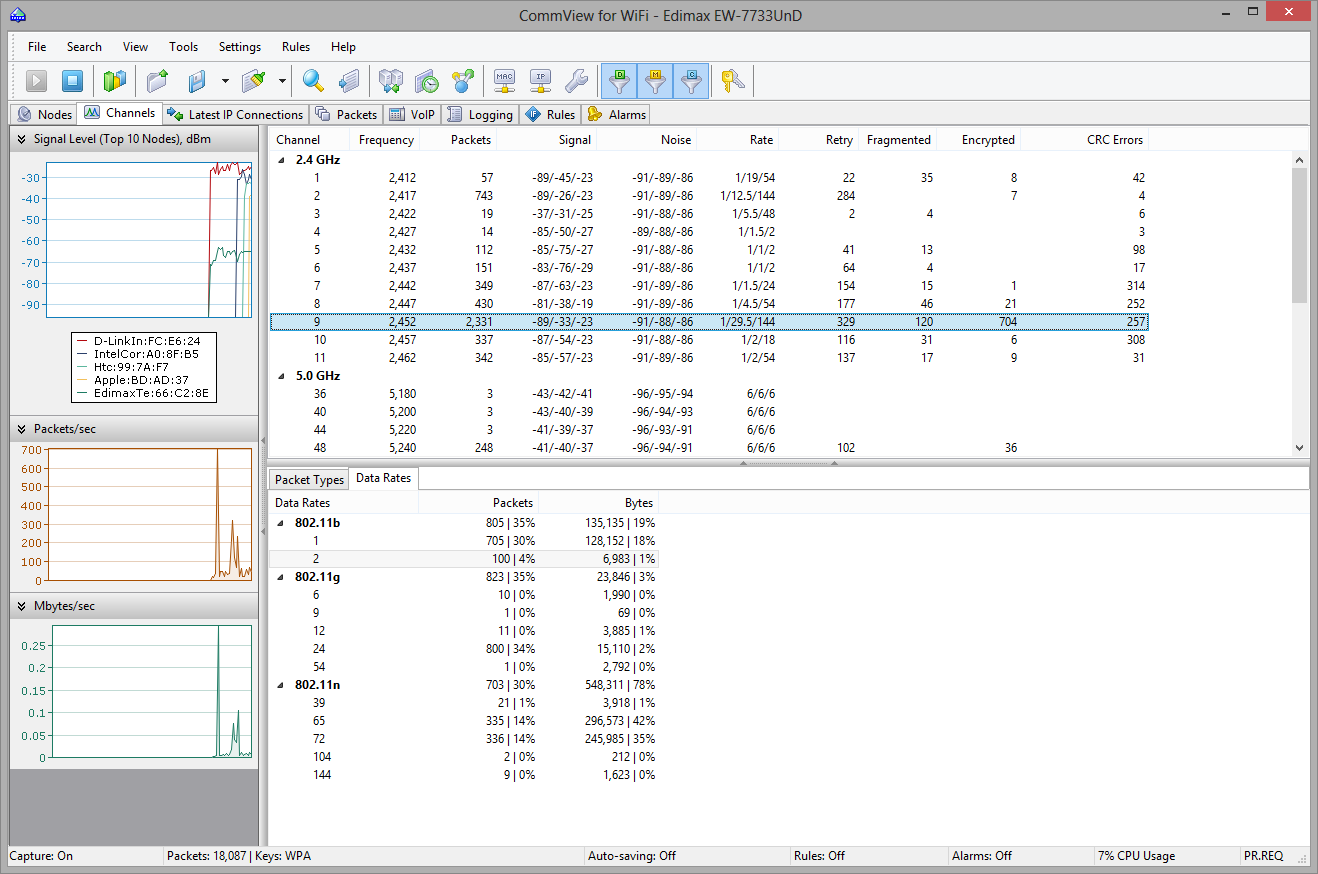
Because the 802.11 standard uses overlapping channel frequencies in the 2.4 GHz band, you might notice that even if your WLAN is configured to use only one channel, e.g. 6, you will still see non-zero values for the adjacent channels. Unlike 2.4 GHz channels, 5 GHz channels do not overlap.
On the bottom pane, you can see Packet Types and Data Rates tables. These tables display detailed statistics for the selected channel based on the packet types and subtypes and on the data rates.
On the left pane, you can see three charts: Signal Level, Packets/sec, and Mbytes/sec. The Signal Level chart displays the signal level for the top ten nodes found on the selected channel. The Packets/sec and Mbytes/sec charts show the number of packets and Mbytes per second captured on the selected channel. When working with information provided on these charts, please note the following:
- The charts display data for the selected channel only.
- The charts are updated only when the application actually captures data on the select channel. This means that if, for example, you are capturing data on channel 2 and select channel 2 from the channel list, the charts will be constantly updated. If you select channel 3, the charts will be "frozen." If you work in Scanner Mode and select any channel, the charts will be updated every time the application sweeps through the selected channel.
The meaning of the channel's table columns is explained below:
- Channel – channel number.
- Frequency – channel frequency in MHz.
- Packets – the total number of captured packets.
- Signal – signal level in the min/average/max format. The average value is calculated since the data in this table was last reset. Please refer to the Understanding Signal Strength chapter for more information.
- Noise – noise level in the min/average/max format. The average value is calculated since the data in this table was last reset. Noise information may not be available from all adapters. If your adapter does not support it, this column will not be visible.
- Rate – data transfer rate in the min/average/max format. The average value is calculated since the data in this table was last reset.
- Retry – the number of packets where the Retry flag was set.
- Fragmented – the number of packets for which the Fragmented flag was set.
- Encrypted – the number of Data packets for which the Encrypted flag was set.
- CRC Errors – the number of packets with CRC errors. See Understanding CRC and ICV Errors for a detailed explanation.
You can show or hide individual columns by right-clicking on list header or using the View => Channels Columns menu. The column order can be changed by dragging the column header to a new location. Right-clicking on the channel list brings up a menu with the following commands:
- Quick Filter – finds the packets sent on the selected channel and displays them in a new window.
- Save Channels As – allows you to save the contents of the Channels tab as an HTML report.
- Clear Channels – clears the table.
- More Statistics – shows a window with data transfer and protocol distribution statistics.
Right-clicking on the Packet Types and Data Rates tables brings up a menu with the following command:
- Quick Filter – finds the packets with the selected packet type or data rate and displays them in a new window.
Latest IP Connections
This tab is used for displaying detailed information about WLAN connections (IP and IPv6 protocols only). To start capturing packets, select File = > Start Capture in the menu, or click on the corresponding button on the toolbar. Please note that this tab will not be populated unless the program is capable of decrypting WEP/WPA-encrypted WLAN traffic. If your WLAN uses WEP or WPA encryption, all the data packets being sent are encrypted, and it is impossible to obtain information about their IP address unless you have entered the correct decryption key by clicking Settings => WEP/WPA Keys in the menu. Additional steps are required in case of WPA decryption; see Understanding WPA Decryption.
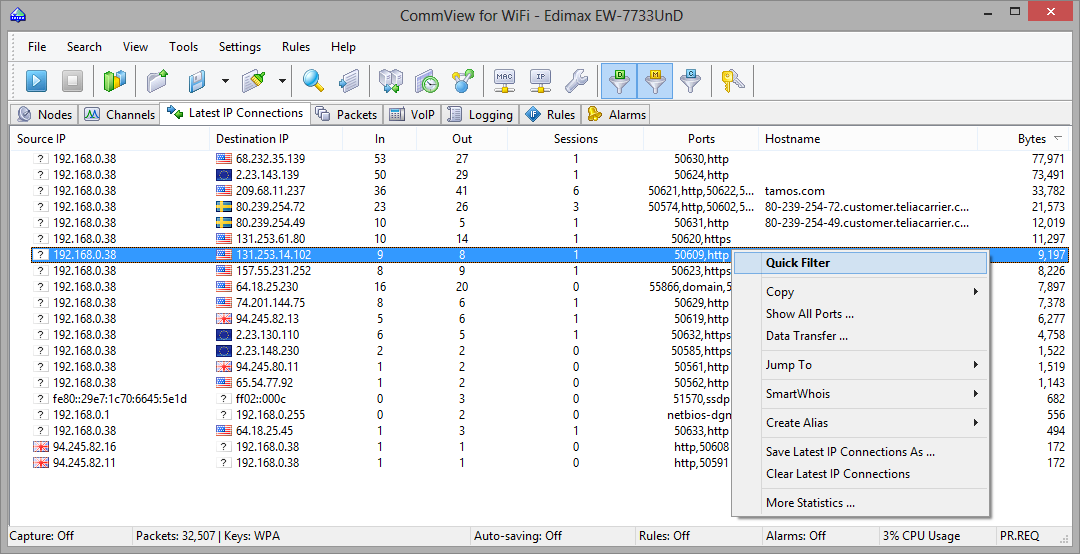
The meaning of the table columns is explained below:
- Source IP, Destination IP – shows the pair of IP addresses between which the packets are being sent. The program automatically determines the location of any IP address, and depending on your geolocation settings, may show the country name or flag next to the IP address. For more information, see Setting Options.
- In – shows the number of packets received.
- Out – shows the number of packets sent.
- Sessions – shows the number of established TCP/IP sessions. If no TCP connections were established (connections failed, or the protocol is UDP/IP or ICMP/IP), this value is zero.
- Ports – lists the remote computer's ports used during the TCP/IP connection or connection attempt. This list can be empty if the protocol is not TCP/IP. Ports can be displayed either as numeric values or as the corresponding service names. For more information, see Setting Options.
- Hostname – shows the remote computer's hostname. If the hostname cannot be resolved, this column is empty.
- Bytes – shows the number of bytes transmitted during the session.
- Last packet – shows the time of the last packet sent/received during the session.
You can show or hide individual columns by right-clicking on list header or using the View => Latest IP Connections Columns menu. The column order can be changed by dragging the column header to a new location. Right-clicking on the Latest IP Connections list brings up a menu with the following commands:
- Quick Filter – finds the packets sent between the selected IP addresses and displays them in a new window. The same action is performed when you double-click on this window.
- Copy – copies the local IP address, remote IP address, or hostname to the clipboard.
- Show All Ports – displays a window with the complete list of ports used in communicating between the selected pair of IP addresses. This is useful when many ports were used, and they do not fit into the corresponding column.
- Data Transfer – displays a window with information on the data transfer volume between the selected pair of IP addresses and the time of the last packet.
- Jump To – allows you to jump to the first/last packet with the selected source/destination IP address; the program will display the Packets tab and set the mouse cursor to the packet that matches the criterion.
- SmartWhois – sends the selected source or destination IP address to SmartWhois, if it is installed on your system. SmartWhois is a stand-alone application developed by our company, capable of obtaining information about any IP address or hostname in the world. It automatically provides information associated with an IP address, such as domain, network name, country, state or province, city. The program can be downloaded from our site.
- Create Alias – brings up a window where you can assign an easy-to-remember alias to the selected IP address.
- Save Latest IP Connections As – allows you to save the contents of the Latest IP Connections tab as an HTML report.
- Clear Latest IP Connections – clears the table.
- More Statistics – shows a window with data transfer and protocol distribution statistics.
Packets
This tab is used for listing all captured network packets and displaying detailed information about a selected packet.
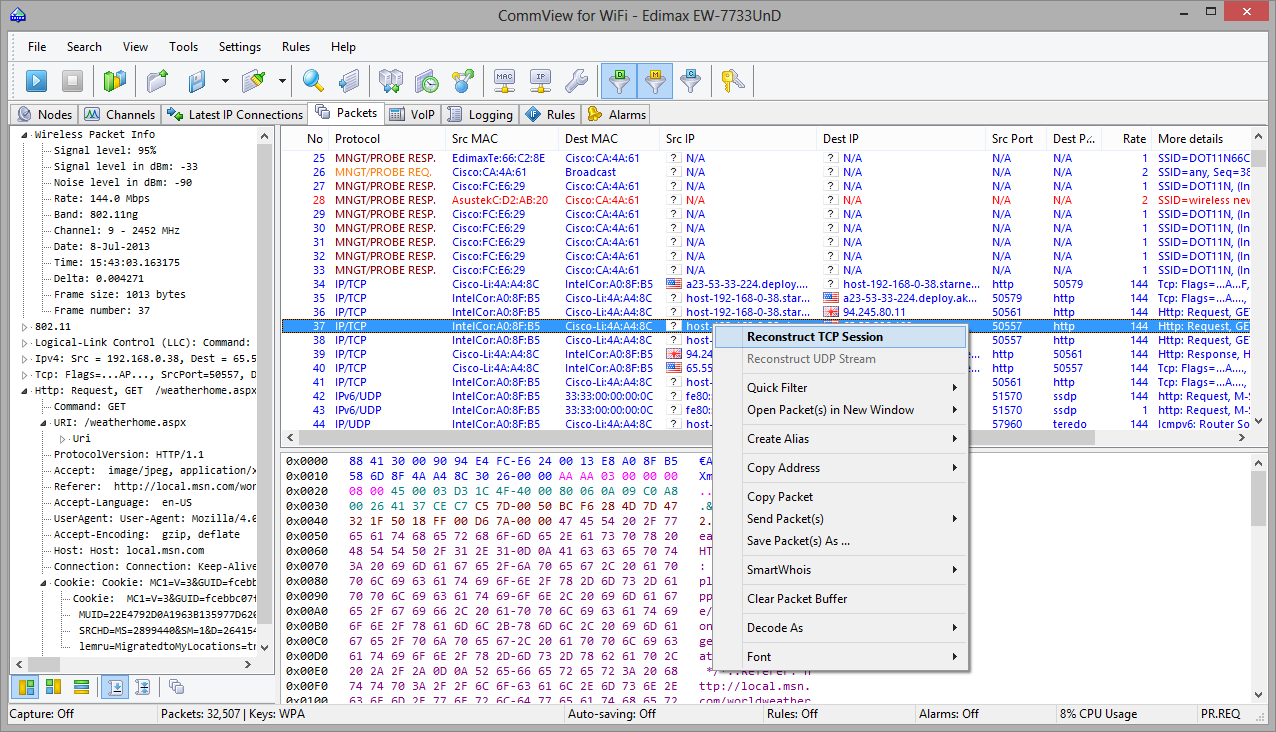
The top table displays the list of captured packets. Use this list for selecting a packet that you want to have displayed and analyzed. When you select a packet by clicking on it, other panes show information about the selected packet.
The meaning of the table columns is explained below:
- No – a unique packet number.
- Protocol – shows the packet's protocol.
- Src MAC, Dest MAC – shows the source and destination MAC addresses.
- BSSID – shows the AP's MAC addresses (where applicable).
- Src IP, Dest IP – shows the source and destination IP addresses (where applicable).
- Src Port, Dest Port – shows the source and destination ports (where applicable). Ports can be displayed either as numeric values or as the corresponding service names. For more information, see Setting Options.
- Time / Delta – shows the packet's absolute or delta time. Delta time is the difference between the absolute times of the last two packets. You can switch from absolute to delta time by clicking View =>Packets Columns =>Show Time As.
- Size – shows packet size in bytes. This column is not visible by default.
- Signal – shows signal strength in percentile or dBm format. Please refer to the Understanding Signal Strength chapter for more information.
- Rate – shows data transfer rate in Megabits per second.
- More Details – shows a brief packet summary.
- Errors – shows information of the errors. See Understanding CRC and ICV Errors for a detailed explanation. This column is not visible by default.
- RA IP – if you use Remote Agent(s) to collect data, displays the IP address of the Remote Agent that captured the corresponding packet.
You can show or hide individual columns by right-clicking on list header or using the View => Packets Columns menu. The column order can be changed by dragging the column header to a new location.
The packet output can be suspended by clicking File =>Suspend Packet Output. In the Suspended mode, the packets are being captured, but not displayed, on the Packets tab. This mode is useful when you are interested only in the statistics rather than individual packets. To resume real-time packets display, click File =>Resume Packet Output.
The middle pane displays the raw contents of the packet, both in hexadecimal notation and as plain text. In the plain text, non-printable characters are replaced with dots. When multiple packets are selected in the top table, the middle pane displays the total number of selected packets, the total size, and the time span between the first and the last packet.
The bottom pane displays decoded packet information for the selected packet. This information includes vital data that can be used by network professionals. Right-clicking on the pane invokes the context menu that allows you to collapse/expand all the nodes or to copy the selected or all nodes.
The packets tab also includes a small toolbar shown below:
![]()
You can change the position of the decoder window by clicking on one of the three buttons on this toolbar (you can have a bottom-, left-, or right-aligned decoder window). The fourth button makes the packet list auto-scroll to the last packet received. The fifth button keeps the packet you selected in the list visible (i.e. it will not leave the visible area as new packets arrive). The sixth button allows you to open the contents of the current packet buffer in a new window. This functionality is very useful under a heavy network load, when the packet list is rapidly scrolling and it is difficult to examine packets before they move out of the visible area. Clicking on this button creates a snapshot of the buffer so you can comfortably examine it in a separate window. You can make as many snapshots as you wish.
Right-clicking on the packet list brings up a menu with the following commands:
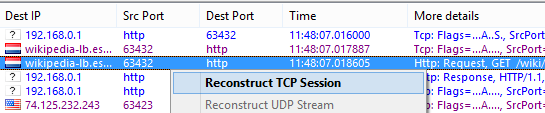
- Reconstruct TCP Session – allows you to reconstruct a TCP session starting from the selected packet; it opens a window that displays the entire conversation between two hosts. The same action is performed when you double-click on this window.
- Reconstruct UDP Stream – allows you to reconstruct a UDP stream starting from the selected packet; it opens a window that displays the entire conversation between two hosts.
- Quick Filter – finds the packets sent between the selected MAC addresses, IP addresses, or ports and displays them in a new window.
- Open Packet(s) in New Window – allows you to open one or several selected packets in a new window for comfortable examination.
- Create Alias – brings up a window where you can assign an easy-to-remember alias to the selected MAC or IP address.
- Copy Address – copies the source MAC address, destination MAC address, source IP address, or destination IP address to the clipboard.
- Copy Packet – copies the raw data of the selected packet to the clipboard.
- Save Packet(s) As – saves the contents of the selected packet(s) to a file. The Save As dialog allows you to select the format to be used when saving data from the drop-down list.
- SmartWhois – sends the source or destination IP address from the selected packet to SmartWhois if it is installed on your system. SmartWhois is a stand-alone application developed by our company capable of obtaining information about any IP address or hostname in the world. It automatically provides information associated with an IP address, such as domain, network name, country, state or province, and city. The program can be downloaded from our site. This option is disabled for non-IP packets.
- Clear Packet Buffer – clears the contents of the program's buffer. The packet list will be cleared, and you will not be able to view the packets previously captured by the program.
- Decode As – for TCP and UDP packets, allows you to decode supported protocols that use non-standard ports. For example, if your SOCKS server runs on port 333 rather than 1080, you can select a packet that belongs to the SOCKS session and use this menu command to make CommView for WiFi decode all packets on port 333 as SOCKS packets. Such protocol-port reassignments are not permanent and will last only until the program is closed. Note that you cannot override standard protocol-port pairs, e.g. you cannot make CommView for WiFi decode packets on port 80 as TELNET packets.
- Font – allows you to increase or decrease the font size used to display packets without affecting the font size of all other interface elements.
You can also drag-and-drop selected packet(s) to the desktop.
Logging
This tab is used for saving captured packets to a file on the disk. CommView for WiFi saves packets in its own format with the .NCFX extension. You can open and view these files at any time using Log Viewer, or you can simply double-click on any NCFX file to have it loaded and decoded. NCFX is an open format; please refer to CommView Log Files Format chapter for detailed NCFX format description.
Save and Manage
Use this frame to save the captured packets manually to a file and to concatenate/split capture files. It is possible either to save all packets currently stored in the buffer or save only a part of them within a given range. The To and From fields allow you to set the necessary range based on the packet numbers as shown on the Packets tab. Click Save As … to select a file name. To concatenate manually multiple NCFX files into a single, larger file, click on the Concatenate Logs button. To split NCFX files that are too large into smaller chunks, click on the Split Logs button. Then the program will guide you through the process, and you will be able to enter the desired size of the output files.
Auto-saving
Check this box to have the program automatically save captured packets as they arrive. Use the Maximum directory size field to limit the total size of the capture files stored in the Log Directory. If the total size of the capture files exceeds the limit, the program automatically deletes the oldest files in the directory. The Average Log File Size field allows you to specify the approximate desired size of each log file. When the log file reaches the specified size, a new file is automatically created. To change the default Log Directory, click on the Save files to box and select a different folder.
If you want to have an important capture file stored for a long time, do not keep it in the default Log Directory: there is a chance it will be automatically deleted as new files are being saved. Move the file to a different folder to preserve it.
Please note that the program does not save each packet individually immediately upon arrival. It means that if you view the log file in real time, it may not contain the latest packets. To make the program immediately dump the buffer to the log file, either click Stop Capture or uncheck the Auto-saving box.
WWW Access Logging
Check this box to enable logging of HTTP sessions. Use the Maximum file size field to limit the size of the log file. If the log file size exceeds the limit, the program automatically deletes the oldest records in the file. To change the default file name and path, click on the Save files to box and select a different file name. Log files can be generated in HTML or TXT formats. Click Configure to change the default logging options. You can change the port number that is used for HTTP access (the default value of 80 might not work for you if you are behind a proxy server), and exclude certain data types (usually logging anything other than HTML pages is quite useless; therefore, it is a good idea to exclude URLs of pictures from the log file).
Viewing Logs
Log Viewer is a tool for viewing and exploring capture files created by CommView for WiFi and several other packet analyzers. It has the functionality of the Packets tab of the main program window, but unlike the Packets tab, Log Viewer displays packets loaded from the files on the disk rather than the packets captured in real time.
To open Log Viewer, click File => Log Viewer in the program's main menu, or just double-click on any CommView for WiFi capture file that you have previously saved. You can open as many Log Viewer windows as you wish, and each of them can be used for exploring one or several capture files.
Log Viewer can be used for exploring capture files created by other packet analyzers and personal firewalls. The current version can import files in the Network Instruments Observer®, Network General Sniffer® for DOS/Windows, Microsoft® NetMon, WildPackets EtherPeek™ and AiroPeek™, Wireshark/Tcpdump, and Wireshark/pcapng formats. These formats are also used by a number of 3rd-party applications. Log Viewer is capable of exporting packet data by creating files in the Network Instruments Observer®, Network General Sniffer® for DOS/Windows, Microsoft® NetMon, WildPackets EtherPeek™ and AiroPeek™, Wireshark/Tcpdump, and Wireshark/pcapng formats, as well as the native CommView format.
Using Log Viewer is similar to using the Packets tab of the main window; please refer to the Packets chapter if you need detailed information.
Log Viewer Menu
File
- Load CommView Logs – opens and loads one or several CommView for WiFi capture files.
- Import Logs – allows you to import capture files created by other packet analyzers.
- Export Logs – allows you to export the displayed packets to capture files in several formats.
- Clear Window – clears the packet list.
- Generate Statistics – makes CommView for WiFi generate statistics on the packets loaded in Log Viewer. Optionally, it is possible to reset previously collected statistical data displayed in the Statistics window. Please note that this function will not show packet distribution along the timeline. It is limited to displaying totals, protocol charts, and LAN hosts tables.
- Send to VoIP Analyzer – sends all packets from the current Log Viewer window to a new VoIP Log Viewer window for VoIP-specific analysis.
- Close Window – closes the window.
Search
- Find Packet – shows a dialog that allows you to find packets matching a specific text.
- Go to Packet Number - shows a dialog that allows you to jump to a packet with the specified number.
Rules
- Apply – applies your current rule set to the packets displayed in Log Viewer. As a result, when you use this command the program will delete the packets that do not match the current rule set. Note that this will not modify the file on the disk.
- From File … - does the same as the Apply command, but allows you to use a rule set from a previously saved .RLS file rather than the current rule set.
Rules
CommView for WiFi allows you to set two types of rules:
- The first type (wireless rules) allows you to filter packets based on the wireless packet type: Data, Management, and Control packets. To turn capturing of these packet types on or off, use the Rules command of the program's menu, or the corresponding toolbar buttons. Additionally, the Ignore Beacons menu command allows you to switch capturing of beacon packets on and off.
- The second type (conventional rules) allows you to filter packets based on many criteria, such as port number or MAC address. To use this type of rule, switch to the Rules tab of the program's main window. If one or more rules are set, the program filters packets based on the set rules and displays only the packets that comply with these rules. If a rule is set, the name of the corresponding page is displayed in bold font.
The program's status bar shows the number of conventional rules that are currently active. Note that it does not show the number of active wireless rules, as the state of the toolbar buttons (up or down) clearly indicate if any of the wireless rules are on or off. Also, note that wireless rules have precedence over conventional rules. Any captured packet must first pass the wireless rules before any further processing takes place. If, for example, none of the three wireless rules toolbar buttons is pressed, the program will not display any packets.
You can save your rules configuration(s) to a file and load them by using the Rules command of the program's menu.
Since WLAN traffic can often generate a high number of packets, it is recommended that you use rules to filter out unnecessary packets. This can considerably reduce the amount of system resources consumed by the program. If you want to enable/disable a rule, select the appropriate branch on the left side of the window (e.g. IP Addresses or Ports), and check or uncheck the box describing the rule (Enable IP Address rules or Enable port rules). Available types of rules are overviewed below.
Protocols
Allows you to ignore or capture packets based on Ethernet (Layer 2) and IP (Layer 3) protocols.
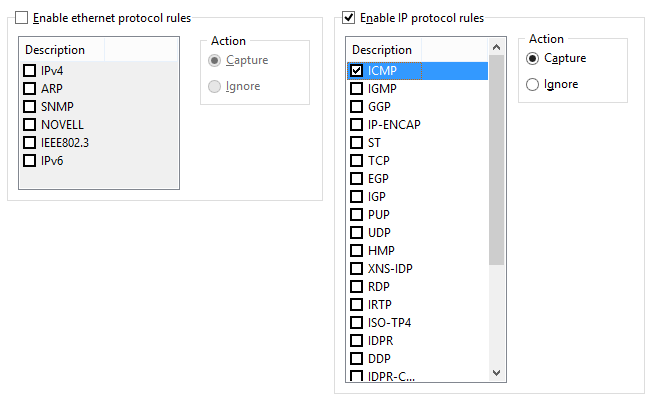
This example shows how to make the program capture only ICMP and UDP packets. All other packets in the IP family will be ignored.
MAC Addresses
Allows you to ignore or capture packets based on MAC (hardware) addresses. Enter a MAC address in the Add Record frame, select the direction (From, To, or Both), and click Add MAC Address. The new rule will be displayed. Now you can select the action to be taken when a new packet is processed: the packet can be either captured or ignored. You can also click on the MAC Aliases button to get the list of aliases; double-click on the alias you would like to add, and the corresponding MAC address will appear in the input box.
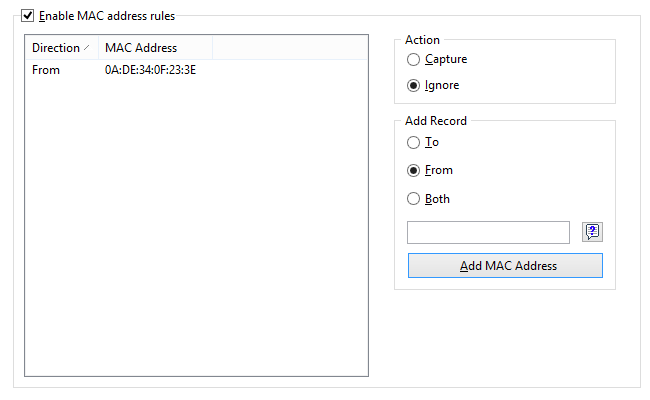
This example shows how to make the program ignore packets that come from 0A:DE:34:0F:23:3E. All packets that come from other MAC addresses will be captured.
IP Addresses
Allows you to ignore or capture packets based on IP addresses. Enter an IP or IPv6 address in the Add Record frame, select the direction (From, To, or Both), and click Add IP Address. You can use wildcards to specify blocks of IP addresses. The new rule will be displayed. Now you can select the action to be taken when a new packet is processed: the packet can be either captured or ignored. You can also click on the IP Aliases button to access the list of aliases; double-click on the alias you would like to add, and the corresponding IP address will appear in the input box.
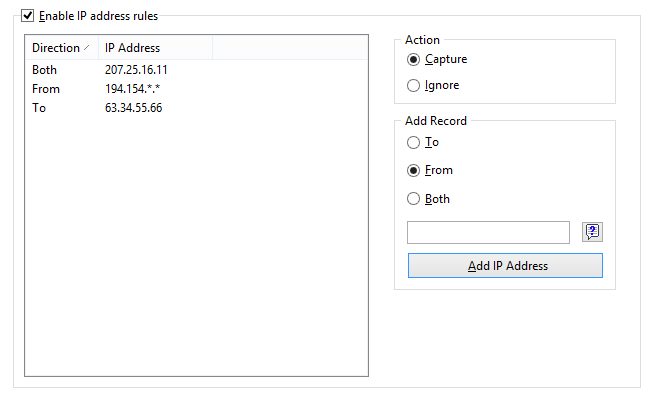
This example shows how to make the program capture the packets that go to 63.34.55.66, go to and come from 207.25.16.11 and come from all addresses between 194.154.0.0 and 194.154.255.255. All packets that come from other addresses or go to other addresses will be ignored. Since IP addresses are used in the IP protocol, such configuration will automatically make the program ignore all non-IP packets. Usage of IPv6 addresses requires Windows XP or higher and that the IPv6 stack be installed.
Ports
Allows you to ignore or capture packets based on ports. Enter a port number in the Add Record frame, select the direction (From, To, or Both), and click Add Port. The new rule will be displayed. Now you can select the action to be taken when a new packet is processed: the packet can be either captured or ignored. You can also press the Port Reference button to get a list of all known ports; double-click on the port you would like to add and its number will appear in the input box. You can also click on the Port Reference button to get a list of all known ports; double-click on the port you would like to add and its number will appear in the input box. Ports can also be entered as text; for example, you can type in http or pop3, and the program will convert the port name to the numeric value.
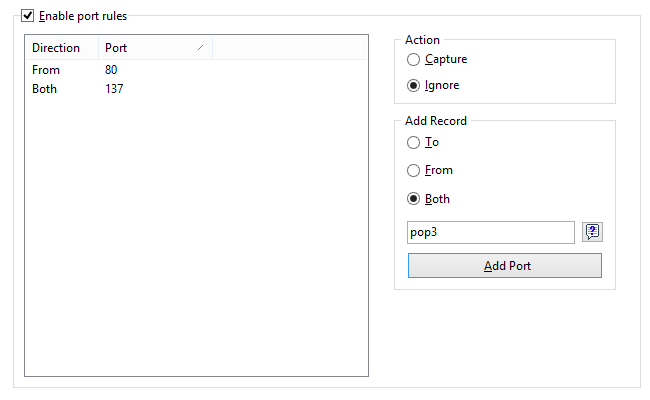
This example shows how to make the program ignore packets that come from port 80 and go to and come from port 137. This rule will prevent CommView for WiFi from displaying inbound HTTP traffic, as well as inbound and outbound NetBIOS Name Service traffic. All packets coming to and from other ports will be captured.
TCP Flags
Allows you to ignore or capture packets based on TCP flags. Check a flag or a combination of flags in the Add Record frame, and click Add Flags. The new rule will be displayed. Now you can select the action to be taken when a new packet with the entered TCP flag is processed: the packet can be either captured or ignored.
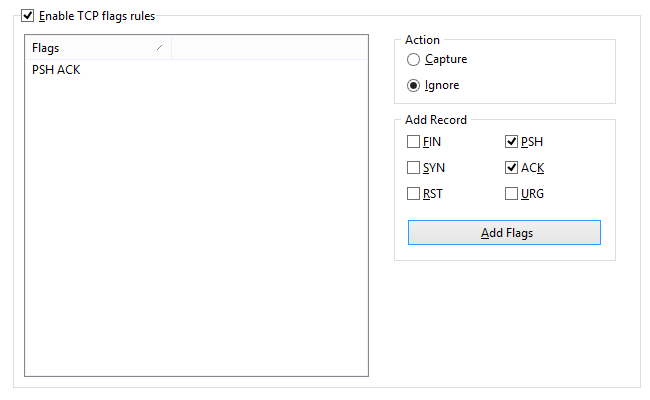
This example shows how to make the program ignore TCP packets with the PSH ACK flag. All packets with other TCP flags will be captured.
Text
Allows you to capture packets that contain certain text. Enter a text string in the Add Record frame and click Add Text. The new rule will be displayed. Now you can select the action to be taken when a new packet is processed: the packet can be either captured or ignored.
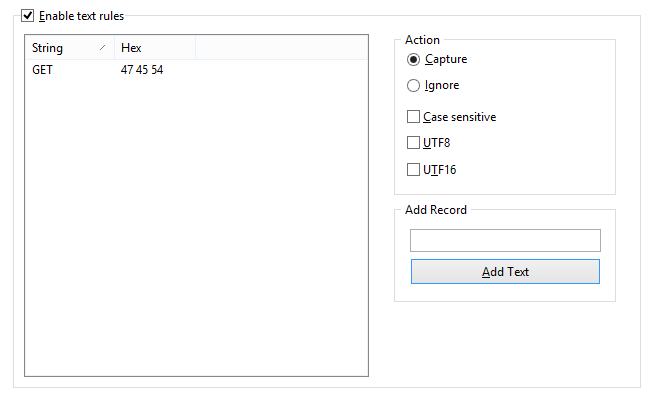
This example shows how to make the program capture only the packets that contain "GET". Check the Case sensitive box if you want the rules to be case-sensitive. Check the UTF8 or UTF16 box if you want the rule to match the text encoded using the respective encodings. All other packets that do not contain the text mentioned above will be ignored. If you would like to create a rule based on hex byte sequences, when the text is not printable (e.g. 0x010203), use the Advanced Rules.
Advanced
Advanced rules are the most powerful and flexible rules that allow you to create complex filters using Boolean logic. For the detailed help on using advanced rules, please refer to the Advanced Rules chapter.
Advanced Rules
Advanced rules are the most powerful and flexible rules that allow you to create complex filters using Boolean logic. Using advanced rules requires a basic understanding of mathematics and logic, but the rules syntax is rather easy to understand.
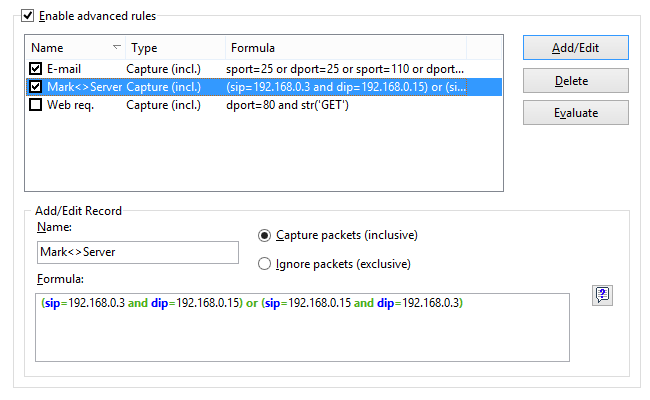
Overview
To add a new rule, you should enter an arbitrary name in the Name field, select the action (Capture/Ignore), enter a Formula using the syntax described below, and click Add/Edit. Your new rule will be added to the list and become active immediately. You can add as many rules as you wish, but only those rules that have a checked box next to the rule name are active currently. You can activate/deactivate rules by checking/unchecking the corresponding boxes or completely delete selected rules using the Delete button. If more than one rule is active, you can evaluate the resulting combined rule by clicking Evaluate. Please note that multiple positive ("Capture") active rules are combined using the logical OR operator, e.g. if you have three active rules, RULE1, RULE2, and RULE3, the resulting rule is RULE1 OR RULE2 OR RULE3. If you also use negative ("Ignore") rules, those will be added to the final expression using the logical AND operator, because combining a negative rule as "OR" would be make no sense.
You can use advanced rules in conjunction with the basic rules described in the previous chapter. However, if you feel comfortable with Boolean logic, it is a good idea to use advanced rules only, as they offer much more flexibility. Basic rules are combined with advanced rules using the logical AND operator.
Syntax Description
- dir – packet direction. Possible values are in (inbound), out (outbound), and pass (pass-through). This keyword is for compatibility with the standard, non-wireless edition of CommView only. In CommView for WiFi, there are no inbound or outbound packets, because your adapter does not participate in data exchange and only passively monitors pass-through packets.
- etherproto – Ethernet protocol, the 13th and 14th bytes of the packet. Acceptable values are numbers (e.g. etherproto=0x0800 for IP) or common aliases (e.g. etherproto=ARP, which is equivalent to 0x0806).
- ipproto – IP protocol. Acceptable values are numbers (e.g. ipproto!=0x06 for TCP) or commonly used aliases (e.g. ipproto=UDP, which is equivalent to 0x11).
- smac – source MAC address. Acceptable values are MAC addresses in hex notation (e.g. smac=00:00:21:0A:13:0F) or user-defined aliases.
- dmac – destination MAC address.
- sip – source IP or IPv6 address. Acceptable values are IP addresses in dotted notation (e.g. sip=192.168.0.1), IP addresses with wildcards (e.g. sip!=*.*.*.255, except for IPv6 addresses), network addresses with subnet masks (e.g. sip=192.168.0.4/255.255.255.240 or sip=192.168.0.5/28), IP ranges (e.g. sip from 192.168.0.15 to 192.168.0.18 or sip in 192.168.0.15 .. 192.168.0.18 ), or user-defined aliases. Use of IPv6 addresses requires Windows XP or higher and that the IPv6 stack be installed.
- dip – destination IP address.
- sport – source port for TCP and UDP packets. Acceptable values are numbers (e.g. sport=80 for HTTP), ranges (e.g. sport from 20 to 50 or sport in 20..50 for any port number between 20 and 50) or the aliases defined by your operating system (e.g. sport=ftp, which is equivalent to 21). For the list of aliases supported by your OS click View => Port Reference.
- dport – destination port for TCP and UDP packets.
- flag – TCP flag. Acceptable values are numbers (e.g. 0x18 for PSH ACK) or one or several of the following characters: F (FIN), S (SYN), R (RST), P (PSH), A (ACK), and U (URG), or the has keyword, which means that the flag contains a certain value. Usage examples: flag=0x18, flag=SA, flag has F.
- size – packet size. Acceptable values are numbers (e.g. size=1514) or ranges (e.g. size from 64 to 84 or size in 64..84 for any size between 64 and 84).
- str – packet contents. Use this function to indicate that the packet must contain a certain string. This function has three arguments: string, position, and case sensitivity. The first argument is a string, e.g. 'GET'. The second argument is a number that indicates the string position (offset) in the packet. The offset is zero-based, i.e. if you are looking for the first byte in the packet, the offset value must be 0. If the offset is not important, use –1. The third argument indicates the case-sensitivity and can be either false (case-insensitive) or true (case-sensitive). The second and third arguments are optional; if omitted, the offset defaults to –1 and the case-sensitivity defaults to false. Usage examples: str('GET',-1,false), str('GET',-1), str ('GET').
- hex – packet contents. Use this function to indicate that the packet must contain a certain hexadecimal byte pattern. This function has two arguments: hex pattern and position. The first argument is a hex value, e.g. 0x4500. The second argument is a number that indicates the pattern position (offset) in the packet. The offset is zero-based, i.e. if you are looking for the first byte in the packet, the offset value must be 0. If the offset is not important, use –1. The second argument is optional; if omitted, the offset defaults to –1. Usage examples: hex(0x04500, 14) , hex(0x4500, 0x0E), hex (0x010101).
- bit – packet contents. Use this function to determine if the specified bit at the specified offset is set to 1, in which case the function returns true. If the specified bit is set to 0 or the specified byte is beyond the packet boundary, the function returns false. This function has two arguments: bit index and byte position. The first argument is the bit index in the byte; the allowed values are 0-7. The index is zero-based, i.e. if you are looking for the eighth bit in the byte, the index value must be 7. The second argument is a number that indicates the byte position (offset) in the packet. The offset is zero-based, i.e. if you are looking for the first byte in the packet, the offset value must be 0. Both arguments are mandatory. Usage examples: bit(0, 14) , bit(5, 1).
ToDS, FromDS, MoreFrag, Retry, Power, MoreData, WEP, Order, Ftype, FsubType, Duration, FragNum, SeqNum - allow you to use 802.11 packet header fields in advanced rules. The names of the operators fully correspond to the packet header fields as described in the 802.11 standard specification. The acceptable values for ToDS, FromDS, MoreFrag, Retry, Power, MoreData, WEP, and Order are 0 or 1. For Ftype, FsubType, Duration, FragNum, and SeqNum operators other numeric values are acceptable.
Please refer to the 802.11 standard specification for the detailed information about 802.11 packet headers fields and their acceptable values.
The keywords described above can be used with the following operators:
- and – Boolean conjunction
- or – Boolean disjunction
- not – Boolean negation
- = – arithmetic equality
- != – arithmetic inequality
- <> – same as above
- > – arithmetic greater-than
- < – arithmetic less-than
- ( ) – parenthesis, control operator precedence rules
All numbers can be in decimal or hexadecimal notation. If you want to use the hexadecimal notation, the number must be preceded by 0x, i.e. you can use either 15 or 0x0F.
Examples
Below you will find a number of examples illustrating the rules syntax. Each rule is followed by our comments about what the rule does. The comments are separated from the actual rule by two slashes.
- (smac=00:00:21:0A:13:0E or smac=00:00:21:0A:13:0F) and etherproto=arp // Captures ARP packets sent by two computers, 00:00:21:0A:13:0E and 00:00:21:0A:13:0F.
- ipproto=udp and dport=137 // Captures UDP/IP packets sent to the port number 137.
- dport=25 and str('RCPT TO:', -1, true) // Captures TCP/IP or UDP/IP packets that contain "'RCPT TO:" and where the destination port is 25.
- not (sport>110) // Captures everything except the packets where the source port is greater than 110.
- (sip=192.168.0.3 and dip=192.168.0.15) or (sip=192.168.0.15 and dip=192.168.0.3) // Captures only the IP packets being sent between two machines, 192.168.0.3 and 192.168.0.15. All other packets are discarded.
- ((sip from 192.168.0.3 to 192.168.0.7) and (dip=192.168.1.0/28)) and (flag=PA) and (size in 200..600) // Captures TCP packets the size of which is between 200 and 600 bytes coming form the IP addresses in the 192.168.0.3 - 192.168.0.7 range, where destination IP address is in the 192.168.1.0/255.255.255.240 segment, and where the TCP flag is PSH ACK.
- Hex(0x0203, 89) and (dir<>in) // Captures the packets that contain 0x0203 at the offset 89, where the packet direction is not inbound.
- not(ftype=0 and fsubtype=8) // Ignore management packets of the beacon type
- ftype=2 and wep=1 // Capture encrypted data packets
- MoreFrag=0 and FragNum=0 // Capture unfragmented packets
Alarms
This tab allows you to create alarms that can notify you about important events, such as suspicious packets, high bandwidth utilization, unknown addresses, etc. Alarms are very useful in a situation where you need to watch the network for some suspicious events, for example distinctive byte patterns in captured packets, port scans, or unexpected hardware device connections.
Alarms can be triggered only by those packets that have passed the program's filters. If, for example, you configured the program to filter out UDP packets by creating the corresponding rule, while one of your alarms is supposed to be triggered by a UDP packet, such an alarm will never be triggered.
Alarms are managed using the alarm list shown below:
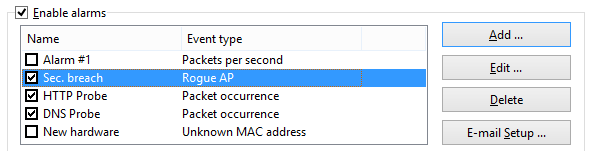
Each line represents a separate alarm, and the checkbox next to the alarm name indicates if the alarm is currently active. When an alarm is triggered, the check mark disappears. To reactivate a deactivated alarm, check the box next to its name. To disable all alarms, uncheck the Enable alarms box. To add a new alarm or edit or delete an existing one, use the buttons to the right of the alarm list. The E-mail Setup button should be used for entering information about your SMTP server if you plan to use e-mail notification options (see below).
The alarm setup window is shown below:
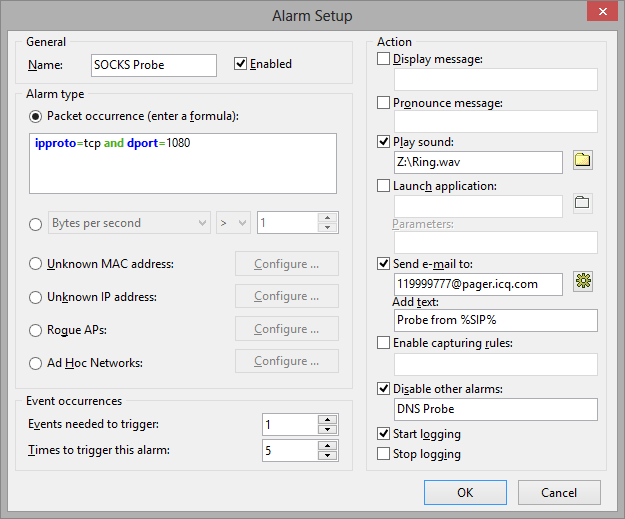
The Name field should be used for describing the alarm function. Check the Enabled box if you want the alarm that you are adding/editing to be activated once you have finished its setup. This check box is equivalent to the one shown in the alarms list. The Alarm Type frame allows you to select one of the ten alarm types:
- Packet occurrence – the alarm will be triggered once CommView for WiFi has captured a packet that matches the given formula. The formula syntax is the same as the syntax used in Advanced Rules and is described in the Advanced Rules chapter in detail.
- Bytes per second – the alarm will be triggered once the number of bytes per second has exceeded (or fallen below) the specified value. Note that you should enter the value in bytes, so if you would like to have the alarm triggered when the data transfer rate exceeds 1Mbyte per second, the value you should enter is 1000000.
- Packets per second – the alarm will be triggered once the number of packets bytes per second has exceeded (or fallen below) the specified value.
- Broadcasts per second – the alarm will be triggered once the number of broadcast packets has exceeded (or fallen below) the specified value.
- Multicasts per second – the alarm will be triggered once the number of multicast packets has exceeded (or fallen below) the specified value.
- CRC errors per second - the alarm will be triggered once the number of CRC errors per second has exceeded (or fallen below) the specified value.
- Retries per second – the alarm will be triggered once the number of retries per second has exceeded (or fallen below) the specified value.
- Unknown MAC address – the alarm will be triggered once CommView for WiFi has captured a packet with an unknown source or destination MAC address. Use the Configure button to enter known MAC addresses. This alarm type is useful for detecting new, unauthorized hardware devices connected to your WLAN.
- Unknown IP address – the alarm will be triggered once CommView for WiFi has captured a packet with an unknown source or destination IP or IPv6 address. Use the Configure button to enter known IP addresses. This alarm type is useful for detecting unauthorized IP connections behind a corporate firewall. Use of IPv6 addresses requires Windows XP or higher and that the IPv6 stack be installed.
- Rogue APs – the alarm will be triggered once CommView for WiFi has captured a beacon packet from an unknown access point. Use the Configure button to enter the MAC addresses of known access points. This alarm type is useful for detecting unauthorized access points.
- Ad Hoc Networks – the alarm will be triggered once CommView for WiFi has captured a beacon packet from an unknown Ad Hoc station. Use the Configure button to enter the MAC addresses of known Ad Hoc stations, if any. This alarm type is useful for detecting unauthorized usage of Ad Hoc networks.
The Events needed to trigger field allows you to specify the number of times the expected event must occur before the alarm is triggered. For example, if you specify the value of 3, the alarm will not be triggered until the event occurs three times. If you edit an existing alarm, the internal event counter will be reset.
The Times to trigger this alarm field allows you to specify the number of times your alarm may be triggered before deactivation. By default, this value equals 1, so the alarm will be disabled after the first event occurrence. By increasing this value, you will make CommView for WiFi trigger the alarm multiple times. If you edit an existing alarm, the internal trigger counter will be reset.
The Action frame allows you to select the actions to be performed when the alarm event occurs. The following actions are available:
- Display message – shows a non-modal message box with the specified text. This action allows use of variables that are to be replaced by the corresponding parameters of the packet that has triggered the alarm. These variables are listed below:
%SMAC% – source MAC address.
%DMAC% – destination MAC address.
%SIP% – source IP address.
%DIP% – destination IP address.
%SPORT% – source port.
%DPORT% – destination port.
%ETHERPROTO% – Ethernet protocol.
%IPPROTO% – IP protocol.
%SIZE% – packet size.
%FILE% – the path to a temporary file that contains the captured packet.
For example, if your message is "SYN packet received from %SIP%," in the actual pop-up window text %SIP% will be replaced by the source IP address of the packet that triggered the alarm. If you use the %FILE% variable, a .NCFX file will be created in the temporary folder. It is your responsibility to delete the file after it has been processed; CommView for WiFi makes no attempt to delete it. You should not use variables if the alarm is triggered by Bytes per second or Packets per second values, as these alarm types are not triggered by individual packets.
- Pronounce message – makes Windows speak the specified text using the text-to-speech engine. This box is disabled if your Windows version does not have the text-to-speech engine. By default, Windows only comes with English computer voices, so Windows may not be able to pronounce messages correctly if the text is entered in a language other than English. You can use the variables described in the Display message section in the message text.
- Play sound – plays the specified WAV file.
- Launch application – runs the specified EXE or COM file. Use the optional Parameters field to enter command line parameters. You can use the variables described in the Display message section above as the command line parameters if you want your application to receive and process information about the packet that triggered the alarm.
- Send e-mail to – sends e-mail to the specified e-mail address. You MUST configure CommView for WiFi to use your SMTP server prior to sending e-mail. Use the E-mail Setup button next to the alarm list to enter your SMTP server settings and send a test e-mail message. Usually, an e-mail message can also be used to send alerts to your instant messaging application, cell phone, or pager. For example, to send a message to an ICQ user, you should enter the e-mail address as ICQ_USER_UIN@pager.icq.com, where ICQ_USER_UIN is the user's unique ICQ identification number, and allow EmailExpress messages in the ICQ options. Please refer to your instant messenger documentation or cell phone operator for more information. The Add text field can be used to add an arbitrary message to the e-mail notification. You can use the variables described in the Display message section in the message text.
- Enable capturing rules – enables Advanced Rules; you should enter the rule name(s). If multiple rules must be enabled, separate them with a comma or semicolon.
- Disable other alarms – disables other alarms; you should enter the alarm name(s). If multiple alarms must be enabled, separate them with a comma or semicolon.
- Start logging – turns on auto-saving (see the Logging chapter); CommView for WiFi will start dumping packets to the hard drive.
- Stop logging – turns off auto-saving.
Click OK to save the settings and close the alarm setup dialog.
All the events and actions related to the alarms will be listed in the Event Log window below the alarm list.
WEP/WPA Keys
The WEP/WPA Keys window allows WEP, WPA, or WPA2 keys to be entered for the decryption of captured packets. Without these keys, the program will not be able to decrypt data packets being transmitted on your WLAN. Since some WLANs use mixed mode encryption, where both WEP- and WPA-enabled clients can authenticate, you can use a WEP key and WPA passphrase simultaneously.
WEP
The standard allows you to use up to four WEP keys, so you can specify one, two, three, or four keys. The key length drop-down list allows you to select the key length. Supported lengths are 64, 128, 152, and 256 bits, and you should enter a hexadecimal string that is 10, 26, 32, or 58 characters long correspondingly.
WPA
The Wi-Fi Protected Access (WPA) standard defines a number of authentication and encryption modes. Not all of them are supported by CommView for WiFi due to the restrictions of the underlying security model. CommView for WiFi supports decryption of WPA or WPA2 in Pre-Shared Key (PSK) mode using Temporal Key Integrity Protocol (TKIP) or Advanced Encryption Standard/Counter CBC-MAC Protocol (AES/CCMP) data encryption. You can enter either a passphrase or a hexadecimal key that is 64 characters long.
Please note that packet traffic encrypted with WPA3 cannot be decrypted. WPA3 uses the passphrase only for authentication; decryption is impossible.
Please refer to the Understanding WPA Decryption chapter for detailed information about the way CommView for WiFi processes WPA-encrypted traffic. You may also want to use the Node Reassociation tool once you have entered a new WPA passphrase.
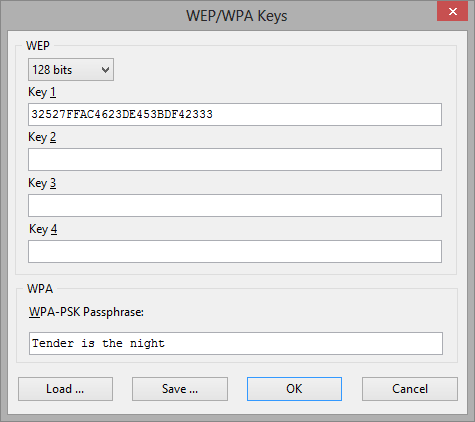
To save the current key set, click Save… . To load a previously saved key set, click Load… .
The key set that you can enter or load using this dialog will be applied to packets captured in real-time, as well as to any NCFX capture files that might have been saved previously. When captured packets are saved to a NCFX capture file, those packets that were decrypted successfully will be saved in decrypted form, while those packets that could not be decrypted will be saved in the original, unmodified form.
Reconstructing TCP Sessions
This tool allows you to view the TCP conversation between two hosts. To reconstruct a TCP session, you should first select a TCP packet on the Packets tab. Depending on the settings (the Search for the session start when reconstructing TCP sessions box in Settings => Options => Decoding), the session will be reconstructed from the selected packet that may be in the middle of the "conversation" or from the session start. After you locate and select the packet, right-click on it and select Reconstruct TCP Session from the pop-up menu as shown below:
Reconstructing sessions works best for text-based protocols, such as POP3, Telnet, or HTTP. Of course, you can also reconstruct a download of a large zipped file, but it can take CommView for WiFi a long time to reconstruct several megabytes of data, and the obtained information would be useless in most of the cases. The Contents tab displays the actual session data, while the Session Analysis tab graphically displays the flow of the reconstructed TCP session.
A sample HTTP session that contains HTML data displayed in ASCII and HTML modes is shown below:
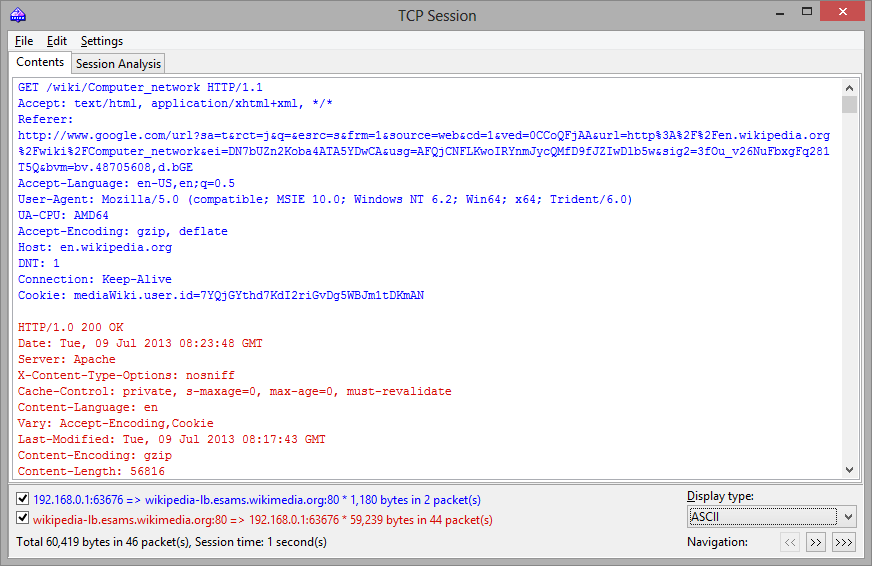
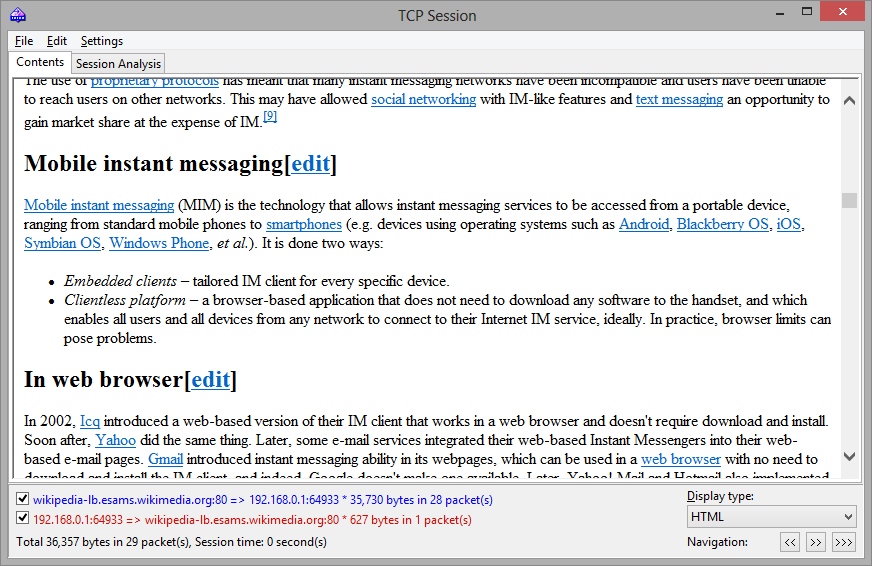
In HTML display mode, HTML pages typically do not include inline graphics, because in HTTP protocol images are transferred separately from HTML data. To view the images, it is usually necessary to navigate to the next TCP session. A sample HTTP session that contains image data displayed in HTML mode is shown below:
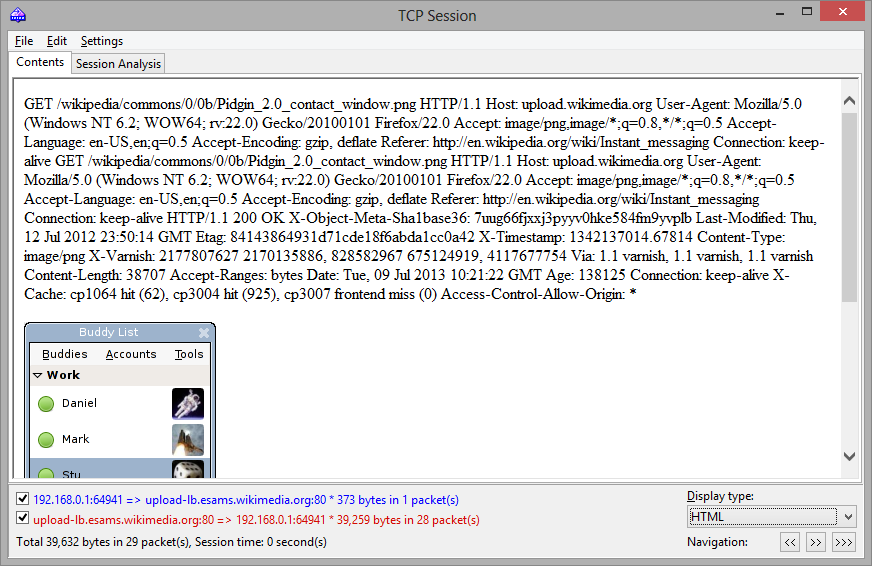
By default, CommView for WiFi attempts to decompress GZIP'd web content and reconstruct images from binary streams. If you want to turn off this functionality, use the Decoding tab of the program's Options dialog.
You can filter out the data that came from one of the directions by unchecking one of the checkboxes on the bottom pane. Incoming and outgoing data are marked with different colors for your convenience. If you want to change one of the colors, click Settings =>Colors and pick a different color. You can enable or disable word wrapping using the Word Wrap item in the Settings menu.
The Display type drop-down list allows you to view data in the ASCII (plain-text data), HEX (hexadecimal data), HTML (web pages and images), EBCDIC (IBM mainframes' data encoding), and UTF-8 (Unicode data) formats. Please note that viewing data as HTML does not necessarily produce exactly the same results as the one you can see in the web browser (e.g. you will not be able to see inline graphics); however, it should give you a good idea of what the original page looked like.
You can choose the default display type for TCP Session Reconstruction window in the Decoding tab of the program's Options dialog.
The Navigation buttons allow you to search the buffer for the next or previous TCP session. The first forward button (>>) will search for the next session between those two hosts that were involved in the first reconstructed session. The second forward button (>>>) will search for the next session between any two hosts. If you have multiple TCP sessions between the two hosts in the buffer and you'd like to see them all one by one, it is recommended to start the reconstruction from the first session, as the back button (<<) cannot navigate beyond the TCP session that was reconstructed first.
The obtained data can be saved as binary data, HTML, text, or rich text file by clicking File =>Save As…. When saving in text format, the resulting file is a Unicode UTF-16 file. When saving in HTML format, the encoding of the resulting file depends on the currently selected Display type. If HTML is currently selected, the resulting file is an ANSI text file; for all other display types, the resulting file is a Unicode UTF-16 file. Note that if you are saving an HTTP session with images, the images in the saved HTML file are stored in the temporary location on your hard drive, so if you want to preserve them, open the saved file in your browser and re-save the file in a format that includes images, such as MHT, before closing CommView for WiFi.
You can search for a string in the session by clicking Edit => Find….
Session Analysis
The Session Analysis tab of the TCP Session window graphically displays the reconstructed TCP session. You can see the session data flow, errors, delays, and retransmissions of lost data.
The following data is displayed for every session packet:
- TCP flags
- Absolute and relative SEQ and ACK values
- Packet arrival time
- Delta time between the current and previous packet
- Packet number in the reconstructed session
If a packet contains errors, the nature of the error is explained. It appears as a text description along the right edge of the graph. When you move the mouse over a packet, its contents are displayed in a hint window if the packet contains any data. Note that the Display type field affects the way the data is decoded in the hint window. A sample session analysis window is shown below:
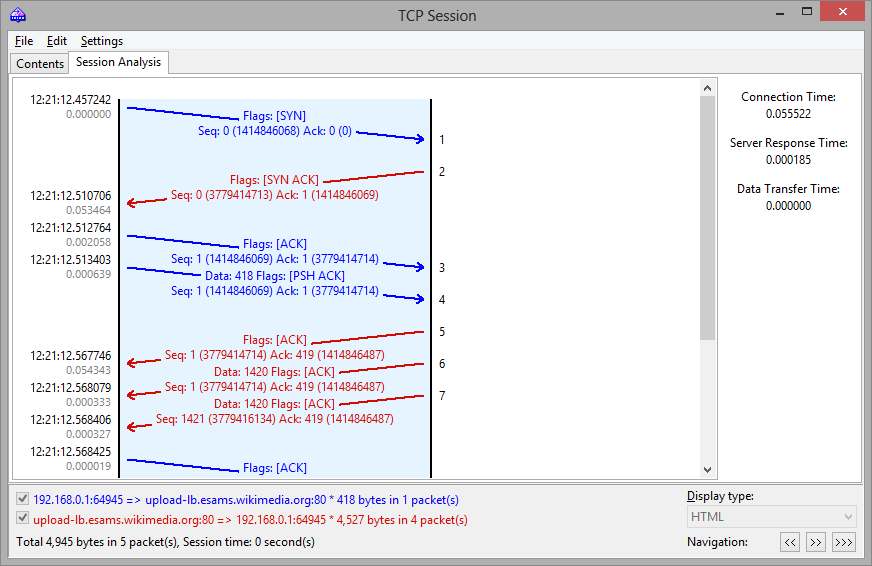
The right pane shows some basic statistics for the given session:
- Connection Time – the time it took to establish the TCP connection. In other words, it's the three-way TCP handshake time (SYN => SYN ACK => ACK).
- Server Response Time – the time elapsed between the initial client request and the server's first data response.
- Data Transfer Time – the time between the server's first and final data responses (0 if there was only one server response).
You can save the graphic layout of the reconstructed TCP session as a BMP, GIF, or PNG file by right-clicking on the layout and selecting the Save Image As… menu item of the context menu. Sessions with a large number of packets will be split into multiple files.
Reconstructing UDP Streams
This tool is very similar to the TCP session reconstruction tool described in the previous chapter; please refer to it for more information. However, because unlike TCP, UDP is a connectionless protocol, the following distinctions exist between TCP session reconstruction and UDP stream reconstruction:
- There is no Session Analysis tab, as there are no sessions, SEQs or ACKs in UDP.
- Because there are no SYNs or FINs in UDP, all packets between the given pairs of IP addresses and ports are considered to belong to the same stream.
Searching Packets
To find packets matching a specific text or address, use the Find dialog (Search => Find Packet). Enter a search string, select the type of entered information (String or Hex), and then click Find Next. The program will search for packets that match the search criterion and display them on the Packets tab.
You can enter text as a string, hexadecimal value, MAC or IP address. Text string search will be performed in ASCII and Unicode (UTF-8 and UTF-16) formats. A hex string should be used when you want to enter non-printable characters: just type in the hexadecimal string, e.g. AD0A027804. Use of IPv6 addresses requires Windows XP or higher and that the IPv6 stack be installed.
Check Match Case for case-sensitive search. Check At offset to search for a string that begins at a certain offset. Note that the offset indicator is hexadecimal and zero-based (i.e. if you are looking for the first byte in the packet, the offset value is 0). You can also select a search direction, Up or Down.
Statistics and Reports
This window (View => Statistics) displays vital network statistics of your WLAN segment, such as packets per second rate, bytes per second rate, Ethernet protocols, and IP protocols and sub-protocols distribution graphs. You can copy any of the graphs to the clipboard by double-clicking on the graph. Ethernet protocols, IP protocols and sub-protocols "pie" graphs can be rotated using the small buttons in the lower right corner for better visibility of the slices.
The data displayed on each page can be saved as a bitmap or comma-delimited text file using the context menu or drag-and-drop. The Report page allows you to have CommView for WiFi automatically generate customizable reports in HTML or comma-delimited text formats.
Network statistics can be collected either by using all the data that passes through your network adapter or by using the rules that are currently set. If you want the statistics counters to process only the data (packets) that match the current rule set and ignore all other data, you should check the Apply current rules box.
General
Displays Packets per second and Bytes/Bits per second histograms, a bandwidth utilization gauge (traffic per second divided by the wireless adapter speed), as well as the overall packet and byte counters. Double-clicking on the gauge brings up a dialog window that allows you to manually configure the adapter speed to be used in the bandwidth utilization calculations.
Protocols
Displays the distribution of the Ethernet protocols, such as ARP, IP, SNAP, SPX, etc. Use the Chart by drop-down list to select one of the two available calculation methods: by number of packets or by number of bytes. If your WLAN uses WEP or WPA encryption, you must configure the WEP or WPA keys correctly to be able to decrypt network traffic; otherwise, this chart will be empty.
IP Protocols
Displays the distribution of the IP protocols. TCP, UDP, and ICMP. Use the Chart by drop-down list to select one of the two available calculation methods: by number of packets or by number of bytes. If your WLAN uses WEP or WPA encryption, you must configure the WEP or WPA keys correctly to be able to decrypt network traffic; otherwise, this chart will be empty.
IP Sub-protocols
Displays the distribution of the main IP application-level sub-protocols: HTTP, FTP, POP3, SMTP, Telnet, NNTP, NetBIOS, HTTPS, and DNS. To add more protocols, click on the Customize button. This dialog allows you to define up to 8 custom protocols. You should enter a protocol name, select the IP protocol type (TCP/UDP), and port number. Use the Chart by drop-down list to select one of the two available calculation methods: by number of packets or by number of bytes. If your WLAN uses WEP or WPA encryption, you must configure the WEP or WPA keys correctly to be able to decrypt network traffic; otherwise, this chart will be empty.
Sizes
Displays the packet size distribution chart.
Hosts by MAC
Lists active WLAN hosts by MAC address and displays data transfer statistics. You can assign aliases to MAC addresses. If you have too many multicast packets on your network and the Hosts by MAC table is overpopulated, you may want to group multicast addresses to one line that will be named GroupedMulticast. You can enable this function by checking the Group multicast addresses box. Please note that only the packets that arrived after this option has been set will be grouped accordingly, the previously received packets will not be affected by this option.
Hosts by IP
Lists active WLAN hosts by IP address and displays data transfer statistics. Since IP packets captured by the program can be originated from an unlimited number of IP addresses (both internal to your WLAN and external), by default this tab does not display any statistics. To have the statistics displayed, you should first set the range of IP addresses to be monitored by clicking Add/Set Ranges. Normally, these ranges should belong to your WLAN, and configuring the program to monitor a certain range of IP addresses allows you to have the usage statistics. You can enter any number of ranges, but the total number of IP addresses being monitored cannot exceed 1,000. To delete a range, right-click on the list of ranges and select the appropriate menu command. You can assign aliases to IP addresses. Additionally, you can check the All box to have the program list all IP addresses; however, this option is not recommended for RAM and CPU utilization reasons. If your WLAN uses WEP or WPA encryption, you must configure the WEP or WPA keys correctly to be able to decrypt network traffic; otherwise, this chart will be empty.
Matrix by MAC
This page displays the graphical conversation matrix between hosts based on their MAC addresses. The hosts represented by their MAC addresses are placed on the circle, and the sessions between them are shown as lines that connect the hosts. Moving the mouse over a host highlights all connections that this host makes with other hosts. You can change the number of the most active host pairs that are displayed in the matrix by changing the value in the Most active pairs field. To change the number of the latest address pairs examined by the program, modify the value in the Latest pairs to count field. If your network segment has many broadcast or multicast packets that overpopulate the matrix, you can ignore such packets by checking the Ignore broadcasts and Ignore multicasts boxes.
Matrix by IP
This page displays the graphical conversation matrix between hosts based on their IP addresses. The hosts represented by their IP addresses are placed on the circle, and the sessions between them are shown as lines that connect the hosts. Moving the mouse over a host highlights all connections that this host makes with other hosts. You can change the number of the most active host pairs that are displayed in the matrix by changing the value in the Most active pairs field. To change the number of the latest address pairs examined by the program, modify the value in the Latest pairs to count field. If your network segment has many broadcast or multicast packets that overpopulate the matrix, you can ignore such packets by checking the Ignore broadcasts and Ignore multicasts boxes. If your WLAN uses WEP or WPA encryption, you must configure the WEP or WPA keys correctly to be able to decrypt network traffic; otherwise, this chart will be empty.
Report
This tab allows you to have CommView for WiFi automatically generate customizable reports in HTML (including images of charts and graphs) or comma -delimited text formats.
It is possible to have the program generate statistics on pre-captured data in addition to real-time statistics. To do that, load a capture file in Log Viewer and click File => Generate Statistic. You can optionally reset previously collected statistics displayed in the Statistics window. Please note that this function will not show packet distribution along the timeline. It is limited to displaying totals, protocol charts, and LAN host tables.
Using Aliases
Aliases are easy-to-remember human-readable names that CommView for WiFi will substitute for a MAC or IP address when showing the packets on the Packets and Statistics tabs. This can make packets easier to recognize and analyze. For example, 00:00:19:2D:0D:35 becomes GATEWAY2, and ns1.earthlink.com becomes MyDNS.
To add a MAC alias right-click on a packet and select Create Alias Using Source MAC or Using Destination MAC from the pop-up menu. A window will pop up where the MAC address field is already filled out, and you will only need to type in an alias. Alternatively, you can click Settings => MAC Aliases… and fill out the MAC address and Alias fields manually. To delete an alias or clear the entire aliases list, right-click on the Aliases window and select Delete Record or Clear All. The same applies to creating IP aliases. When a new IP alias is created by right-clicking on a packet, the alias field is pre-filled with the corresponding hostname (if available) which can then be edited by the user.
Packet Generator
This tool allows you to edit and send packets via your wireless network adapter. To open the Packet Generator, click Tools => Packet Generator, or select a packet from the Packets tab, right-click on it, and select the Send Packet command.
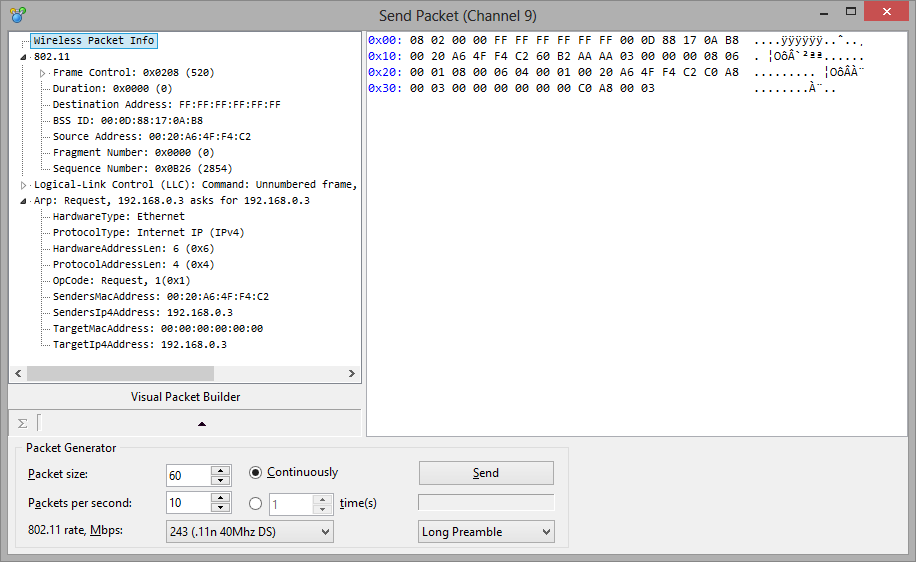
Please read the following important information about the limitations and peculiarities of using in the Packet Generator with wireless adapters:
- Do not use the Packet Generator unless you know exactly what effect you want to achieve. Sending packets may produce unpredictable results, and we strongly recommend refraining from using this tool unless you are an experienced network administrator.
- Your adapter firmware may fail to send certain packets, or it may send certain packets multiple times. This behavior is fully controlled by the firmware and is beyond our control.
- Your adapter firmware may disallow you to send packets at an arbitrary rate. It is quite possible that when you select the rate of 1000 packets per second, the firmware will actually send the packets at a much slower rate.
Please note that the Packet Generator cannot and should not be used for sending application-layer TCP streams, i.e. it cannot take care of incrementing SEQ or ACK values automatically, adjusting checksums and packet sizes and so forth. If you need to send a TCP stream, you should use a Winsock-based application specifically designed for that purpose. The Packet Generator is a tool for replaying pre-captured data, testing firewalls and intrusion detection systems, as well as for performing other specific tasks that require manual packet crafting.
The Packet Generator allows you to change the packet contents and have the packet decode displayed in the left window as you edit it. You can create packets of any kind; you have full control over the packet contents. For IP, TCP, UDP, and ICMP packets, you can automatically correct the checksum(s) by clicking on the Sigma button. To assist you with packet editing, the Visual Packet Builder tool is also available; click on the corresponding button to invoke it.
You can also click on the button with an arrow on it to display the list of available packet templates. The program comes with TCP, UDP, and ICMP packet templates; using them is often faster than typing hex codes in the editor window. These templates contain typical TCP, UDP, and ICMP packets, but you would most probably want to edit many packet fields and use meaningful values that suit your needs, such as real MAC and IP addresses, port numbers, SEQ and ACK numbers, etc. You can use your own templates rather than the built-in ones. You can drag-and-drop a packet from the CommView Packets tab to the Templates section in the Packet Generator window. If you drop several packets into the Templates section, only the first packet will be used as a template. An entry named New Template will appear in the list of templates. You can rename a template by right-clicking on it in the list and selecting Rename. If you need to delete a template, right-click on it and select Delete from the pop-up menu. Selecting a template in the list will load the packet that it contains in the editor window where it can be edited prior to sending.
You can also place NCFX files with the templates of your choice to the TEMPLATES subfolder in the application folder. If CommView for WiFi finds NCFX files (or just one of them) in the TEMPLATES subfolder, it will list them among the available templates in the drop-down list. These NCFX files should contain only one packet per file, but if you use a file that contains many packets, CommView for WiFi will load only the first one.
Once you have edited a packet, use the controls below to send it:
- Packet Size – modifies the packet size.
- Packets Per Second – controls the speed at which packets will be sent.
- Continuously – select this option if you want the Packet Generator to send packets continuously until you click Stop.
- Time(s) – select this option if you want the Packet Generator to send packet a given number of times.
- 802.11 rate – modifies the 802.11 rate to be used for sending packets. Depending on the currently selected band and channel, not all rates may be used. For example, 802.11a packets cannot be sent at the rate of 2 Mbps.
- Long/Short Preamble – sets the preamble type for 802.11b and 802.11g packets. Not applicable to 802.11a.
- Send/Stop – click this button when you are ready to send packets or to stop sending them.
Working with multiple packets
You can use the Packet Generator to send multiple packets at once. To do that, just select the packets you want to send in the list and invoke the Packet Generator using the right-click menu, or drag and drop the selected packets to the Packet Generator window. Alternatively, you can drag and drop capture files in all supported formats directly to the Packet Generator window. When multiple packets are being sent, the packer editor and decoder tree become invisible.
Saving edited packets
If you edited a packet and would like to save it, just drag the decoder tree to the desktop or any folder, and a new file in NCFX format containing the packet will be created. The file name is always PACKET.NCFX. You can also drag the packet to the templates window. If you need to edit and send multiple packets, edit them one by one, each time dragging a new packet to the desktop and renaming it. After that, open a new Log Viewer window, drag-n-drop the edited packets from the desktop to Log Viewer, select them using the Shift button, and invoke the Packet Generator using the context menu.
Visual Packet Builder
Visual Packet Builder is a tool designed for facilitating packet editing and generation in the Packet Generator. This tool allows you to quickly and correctly create a new packet or modify an existing one using ready-made templates. Once created or edited, a packet can be injected into the network using the Packet Generator.
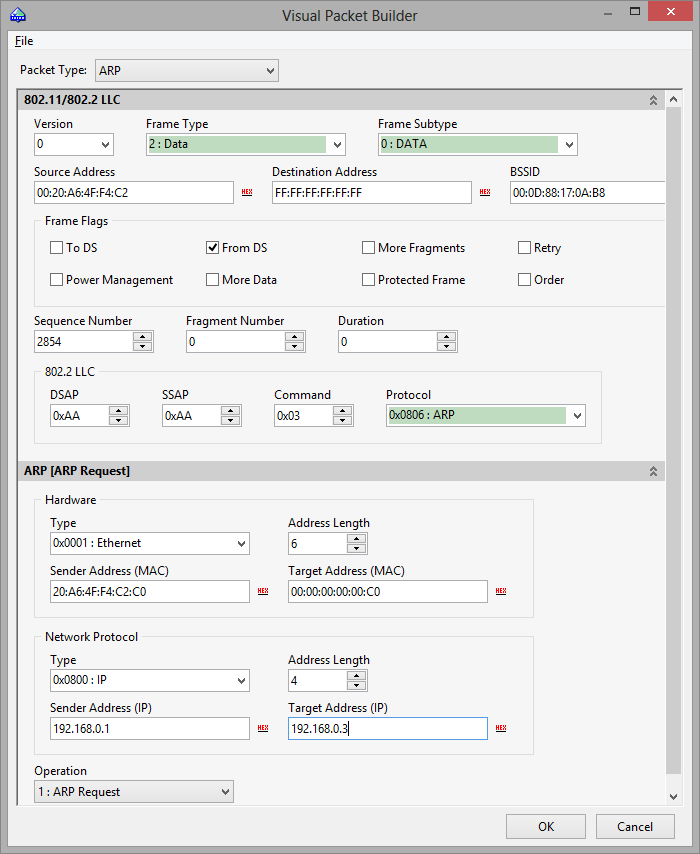
Standard TCP, UDP, and ICMP (based on the 4th and 6th versions of IP protocol), and ARP packet generation is supported. To create a packet, select its type from the Packet Type drop-down list. The default values of the packet fields will be automatically filled in, but can be changed afterwards.
ICMP, TCP, UDP, and ARP packets consist of several encapsulated layers, and the interface of Visual Packet Builder is arranged the same way. Options that correspond to the same layer are located on a separate panel. For example, a TCP packet consists of 4 layers; the Source MAC and Destination MAC address fields are located on the Ethernet II panel (Data link layer), and Src Port and Dst Port values are located on the TCP panel (Transport layer). If you would like to hide a panel, click the Expand/Collapse button located in the right corner of the panel header.
Note that some "parental" layer values affect the packet type on lower layers; hence modifying upper layers may lead to rebuilding the lower layers of a packet. Therefore, if you change the Protocol type in the Ethernet II panel (Data link layer), it will lead to rebuilding the whole packet. Another peculiarity that you should keep in mind is that the values of some fields depend on the contents of other fields, as well as the data contents of the lower layers. Such fields are: checksums and header lengths, and/or data of lower layers. Visual Packet Builder calculates such values automatically. However, when creating non-standard packets, you may want to specify different values manually by checking the Override default value box and specifying the desired values.
Visual Builder helps you control the correctness of the packet being built by highlighting the headers and fields with incorrect or non-standard values in red.
Despite the fact that Visual Packet Builder has internal support for TCP, UDP, ICMP and ARP protocols only, you can still use it to edit packets that use other protocols. For such packets, you can use the hex editor to modify the data.
Once created, a packet can be saved and subsequently loaded to Visual Packet Builder again. Use the respective commands located in the File menu of Visual Packet Builder for loading/saving capture files. You can load any CommView for WiFi capture file (NCFX); however, if the file contains more than one packet, only the first one will be loaded.
NIC Vendor Identifier
The first 24 bits of a network card's MAC address uniquely identify the network card's vendor. This 24-bit number is called the OUI ("Organizationally Unique Identifier"). The NIC Vendor Identifier is a tool that allows you to look up a vendor name by MAC address. To look up a vendor name, click Tools => NIC Vendor Identifier, enter a MAC address, and click Find. The vendor's name will be displayed. By default, CommView for WiFi replaces the first three octets of the MAC address by the adapter vendor name in the Packets tab. This behavior may be changed by unchecking the Display vendor names in MAC addresses checkbox in the General tab of the program Options dialog. The list of vendors is contained in the MACS.TXT file located in the CommView for WiFi application folder. You can manually edit this list to add/modify information.
Scheduler
You can use this tool to create and edit scheduled capturing tasks. This is useful when you want CommView for WiFi to start and/or stop capturing when you are not around, for example, at night or on weekends. To add a new task, click Tools => Scheduler, and then click on the Add button.
Use the Start capturing frame to specify the date and time when CommView for WiFi will start capturing. Use the Channel drop-down list to specify the WLAN channel that should be monitored. Use the Stop capturing frame to specify the date and time when CommView for WiFi will stop capturing. You do not necessarily have to check both Start capturing and Stop capturing boxes. If you check only the first box, capturing would go on until you manually stop it. If you check only the second box, you would have to start capturing manually, but then CommView for WiFi would automatically stop capturing at the specified time.
If CommView for WiFi is already capturing packets at the time when the scheduled task is due and if the adapter you specified is different from the adapter currently being monitored, CommView for WiFi will stop capturing, switch to the adapter you specified, and restart capturing.
It is important to understand that the scheduled tasks can be performed only when CommView for WiFi is running.
Node Reassociation
Given the dynamic nature of WPA encryption, knowing the WPA passphrase alone does not allow you to decrypt traffic immediately after entering the correct passphrase. To be able to decrypt WPA-encrypted traffic, CommView for WiFi must be running and capturing packets during the key exchange phase (key exchange is carried out using the EAPOL protocol). Please refer to the Understanding WPA Decryption chapter for detailed information.
The Node Reassociation tool can be used for initiating a new key exchange:
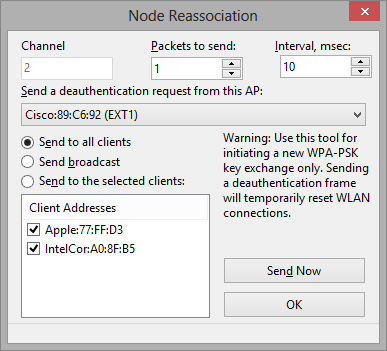
This tool simply sends a deauthentication request to the selected stations on behalf of the access point. This causes the stations to reassociate with the access point. The reassociation process usually takes a second and lets CommView for WiFi capture EAPOL packets necessary for WPA-PSK decryption. Do not use this tool unless you need to decrypt WPA-PSK traffic on your WLAN.
To initiate a reassociation, select an access point from the drop-down list, select the stations, and click Send. The Send to all clients and Send to selected clients options send unicast packets to all or selected clients. The Send broadcast option sends a broadcast packet to the FF:FF:FF:FF:FF:FF address. While this option covers even undetected stations, some stations may ignore broadcast deauthentication requests. You may want to send several packets using the Packets to send and Interval boxes.
Using Remote Agent for WiFi
CommView Remote Agent for WiFi is a companion product that can be used for monitoring network traffic remotely. All you have to do is to install Remote Agent for WiFi on the target computer, and then use CommView for WiFi to connect to Remote Agent. Once you are connected and authenticated, you can start monitoring as if you were there.
This chapter describes how to use CommView for WiFi to connect to Remote Agent and capture traffic remotely. For detailed information on Remote Agent installation and configuration, please refer to the help file that comes with Remote Agent. It is highly recommended that you carefully read the Remote Agent documentation prior to using it. CommView Remote Agent for WiFi can be downloaded from our website.
To switch to remote monitoring mode, click File => Remote Monitoring Mode. An additional toolbar will appear in the CommView for WiFi main window next to the main toolbar. If you are behind a firewall or proxy server, or using a non-standard Remote Agent port, you may need to click on the Advanced Network Settings button to change the port number and/or enter SOCKS5 proxy server settings. The Advanced Network Settings dialog also allows you to define whether Remote Agent will apply the filtering rules locally, or send all the captured traffic to CommView for WiFi; this will be discussed in detail later in this chapter.
Click on the New Remote Agent Connection button to establish a new connection, or click on the Load Remote Agent Profile toolbar button to load a previously saved Remote Agent connection profile. A previously saved profile may also be loaded from the New Remote Agent Connection window.
A Remote Agent Connection window will appear. Enter the IP address of the computer running CommView Remote Agent for WiFi into the IP address input area, enter the connection password and click on the Connect button. If the password is correct, a connection will be established. You will then see the Link Ready message in the status bar and the channel selection box will list the channels supported by the wireless adapter installed on the remote computer. In addition to the channel list, a special Scanner Mode item will be added as the first item on the list.
If you select Scanner Mode, the remote wireless adapter will cycle through the available channels, capturing data from each of them for several seconds. The small button located on the right side of the window, just above the channel selection box, allows you to adjust the scanner settings. Click on this button to select the channels to be monitored in Scanner Mode and set the interval, i.e. the number of seconds per channel.
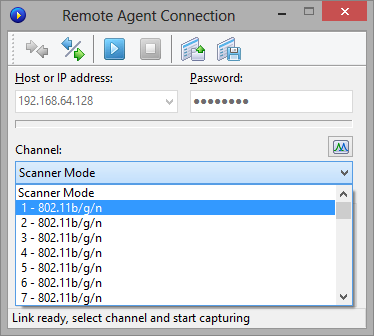
Now is the best time to configure the capturing rules using the Rules tab in the CommView for WiFi main window. You can also apply a custom set of capturing rules to this connection and override the current rules defined in CommView for WiFi by checking the Override current rule set box, clicking on the Edit Formula button and entering the rules formula in the field below. The formula syntax is the same as the one used in Advanced Rules. Once you are ready to start monitoring, select the channel from the list and click the Start Capture toolbar button. CommView for WiFi allows you to save the Remote Agent Connection settings as a connection profile for quick and easy access in the future. Click on the Save Remote Agent profile toolbar button in the New Remote Agent Connection window and enter a name for the file.
CommView for WiFi will start to capture the remote adapter's traffic as if it is your local network traffic; there is virtually no difference between using CommView for WiFi locally or remotely. When you are done with remote monitoring, just click on the Stop Capture toolbar button. You can then change the channel or disconnect from Remote Agent by clicking the Disconnect toolbar button. To return to the standard mode, click File => Remote Monitoring Mode, and the additional toolbar will disappear.
Please note that CommView for WiFi can work with multiple Remote Agents simultaneously. You can open several remote connections, each having its own settings and an independent set of rules and collect the traffic from remote WLANs in one CommView for WiFi instance.
How to Use CommView Remote Agent for WiFi Efficiently
As mentioned before, Remote Agent should be installed on a computer that has a compatible wireless adapter (to be used for monitoring) and Ethernet adapter (to be used for the connection between Remote Agent and CommView for WiFi).
By default, Remote Agent sends all the collected packets back to CommView for WiFi, regardless of the capturing rules that may be configured in CommView for WiFi. This is done for providing correct statistical data and decryption, as well as the means for correct identification of wireless nodes. Since a fully loaded Wi-Fi network may have a bandwidth of about 1 Gbit/s, it's important that the wired link between Remote Agent and CommView for WiFi be capable of handling this bandwidth. In a modern office environment, where Gigabit networks are common, a single Gigabit adapter can easily receive data from a dozen Remote Agents.
There are situations where a fast connection is problematic. For example, a high bandwidth connection may not be available if you are monitoring a remote WLAN over the Internet. Even a T3 connection (4.5 Mbit/s) is insufficient to transfer all packets from a moderately loaded WLAN. In such situations, you can change the default setting and make Remote Agent filter the packets before they are transferred to CommView for WiFi. The Advanced Network Settings button on the additional remote monitoring toolbar in the main CommView for WiFi window allows you to enable the Minimize bandwidth option. When this option is enabled, the current CommView for WiFi rule set is periodically sent to Remote Agent. This rule set is then applied locally, so that only those packets that pass the rules are sent back to CommView for WiFi. In this mode, the Nodes tab may not display any nodes, and the Channels tab will not show full per-channel statistics, so use this mode only when you have limited bandwidth, but still need access to the packets from a remote WLAN.
For the same bandwidth reasons, it is highly recommended to NOT use a wireless connection for exchanging data between Remote Agent and CommView for WiFi. It is also a bad idea because the monitoring wireless adapter would pick up the packets sent by the wireless adapter being used for communicating with CommView for WiFi if they operate on the same or close channels. This will simply cause the snowball effect.
If CommView Remote Agent for WiFi captures more data than it can send to CommView for WiFi, it uses an internal buffer to store the packets that cannot be sent immediately. The buffer size is 5 Mbytes. The Buffer utilization indicator in the Remote Agent window shows the current status of the buffer. For example, if the program has buffered 2.5 Mbytes of data, the buffer utilization is 50%. If/when the buffer utilization reaches 100%, the program stops buffering data and discards captured packets until some buffer space is free.
Security
CommView Remote Agent for WiFi was made with security in mind. It can be accessed only by using a password that is never transmitted in plain text and that is ensured by using a challenge-response protocol with a secure hash function. If the authentication is successful, all transmitted traffic is compressed and then encrypted with the same password. Please take precautions to keep your password secret. Once it is revealed to an unauthorized person, that person will have broad capabilities to study your network and intercept network traffic on the remote computer.
Using RPCAP
This chapter describes experimental functionality that might or might not work as expected depending on the specific implementation in third party software and hardware. No technical support will be provided for this functionality.
In addition to the remote capture functionality provided by CommView Remote Agent, CommView for WiFi can also capture traffic from remote computers using the RPCAP (Remote Packet Capture) protocol. This protocol is supported by some hardware (e.g. Aerohive Access Points) and software (e.g. WinPcap).
To switch to remote monitoring mode, click File => Remote Monitoring Mode. An additional toolbar will appear in the CommView for WiFi main window next to the main toolbar. Click the New RPCAP Connection button to open a new connection window.
To connect to a remote device, enter its hostname or IP address, specify the port number (RPCAP uses port 2002 by default), check the User Authentication box and specify a username and password, if authentication is required, and then check the Promiscuous mode box if that is the capture mode you wish to use. Click Connect to establish a connection. Once the connection has been established, the Adapter drop-down list will be populated by available network interfaces. Click Capture to start capturing.
Using Aruba Remote Capture
This chapter describes experimental functionality that might or might not work as expected depending on the specific implementation in third party software and hardware. No technical support will be provided for this functionality.
In addition to the remote capture functionality provided by CommView Remote Agent, CommView for WiFi can also capture traffic from access points manufactured by Aruba.
To switch to remote monitoring mode, click File => Remote Monitoring Mode. An additional toolbar will appear in the CommView for WiFi main window next to the main toolbar. Click the New Aruba Remote Capture button to open a new connection window.
Remote packet capture must be initiated on the AP side using the command-line interface. Aruba remote capture uses the following syntax:
Example:
Once you have configured remote capture on the AP side, specify the port number that you have chosen and click Connect to begin receiving packets from your Aruba AP.
Port Reference
This window (View => Port Reference) displays a table of port numbers and corresponding service names. This reference is obtained from the SERVICES file installed by Windows. You can find it in the C:\windows\system32\drivers\etc folder. You can manually edit this file if you want to add more ports/service names. CommView for WiFi reads this file on start up, so your changes to the file will be displayed only after you restart the program.
Setting Options
You can configure some of the program's options by selecting Settings => Options in the menu.
General
- Auto-start capturing – check this box if you want CommView for WiFi to start capturing packets immediately after launching the program. Please select the channel that you would like to monitor from the drop-down list.
- Disable DNS resolving – check this box if you do not want CommView for WiFi to perform reverse DNS lookups of the IP addresses. If you check it, the Hostname column on the Latest IP Connections tab will be blank.
- Convert numeric port values to service names – check this box if you want CommView for WiFi to display service names rather than numbers. For example, if this box is checked, port 21 is shown as ftp, and port 23 as telnet. The program converts numeric values to service names using the SERVICES file installed by Windows. You can find it in the C:\Windows\system32\drivers\etc folder. You can edit this file manually if you want to add more ports/service names.
- Convert MAC addresses to aliases – substitute MAC addresses for aliases on the Packets tab. Aliases can be assigned to MAC addresses using the Settings =>MAC Aliases menu command.
- Convert IP addresses to aliases – substitute IP addresses for aliases on the Packets and Statistics tabs. Aliases can be assigned to IP addresses using the Settings =>IP Aliases menu command.
- Convert IP addresses to hostnames in the Packets tab – check this box if you want CommView for WiFi to show resolved hostnames rather than IP addresses in the Packets tab. If this box is checked, CommView for WiFi will first attempt to find an alias for the given IP address. If no alias is found or the previous box (Convert IP addresses to aliases) is not checked, CommView for WiFi will query the internal DNS cache for the hostname. If no hostname is found, the IP address will be displayed in numeric form.
- Display vendor names in the MAC addresses – by default, CommView for WiFi replaces the first three octets of the MAC address by the adapter vendor name in the Packets tab. Uncheck this checkbox if you want to change this behavior.
- Capture Damaged Packets – because of the distance, radio interference, and other physical phenomena, some packets received by your wireless adapter might be damaged, i.e. contain partly or fully invalid data. Check this box if you want the program to capture and display such packets. This option has both drawbacks and advantages. The advantage is that if you are located far away from WLAN stations and/or access points, a high percentage of packets might be broken, and enabling this option would allow you to see more data, even though the data might be partly damaged. However, the drawback is that you would see some packets with invalid data, e.g. you might see IP packets sent to non-existent IP addresses. Also, when this box is checked, the program will try to decrypt those WEP- or WPA-encrypted packets in which the Integrity Check Value is incorrect, but the headers appear to be valid.
Memory Usage
Display
- Maximum packets in buffer – sets the maximum number of packets the program stores in the memory and can display in the packet list (2nd tab). For example, if you set this value to 3000, only the last 3000 packets will be stored in the memory and packet list. The higher this value is, the more computer resources the program consumes.
Note that if you want to have access to a high number of packets, it is recommended that you use the auto-saving features (see Logging for more information): it allows you to dump all the packets into a log file on the hard drive. - Maximum Latest IP Connections lines – sets the number of lines the program displays on the Latest IP Connections tab. When the number of connections exceeds the limit, the connections that have been idle for the longest period of time are removed from the list.
- Driver Buffer – sets the driver buffer size. This setting affects the program's performance: the more memory allocated for the driver buffer, the fewer packets the program drops. For low traffic WLANs, the buffer size is not critical. For high traffic WLANs, you may want to increase the buffer size if the program drops packets. To check the number of dropped packets, use the File => Performance Data menu command while capturing is on.
Latest IP Connections
- Display Logic – allows you to select the Latest IP Connections layout that best suits your needs. Selecting an item from the drop-down list will display the description of the selected logic. In most cases, it is recommended to use the default Smart logic.
- Define Local IP Addresses – you should use this tool if you monitor WLAN traffic with many pass-through packets and a mixture of external and internal IP addresses. In such a situation, CommView for WiFi does not "know" which IP addresses should be treated as local and might reverse the IP addresses in the Source and Destination IP columns. This tool allows you to define the local network addresses and subnet masks to make sure the Latest IP Connections window works correctly. This will work only if you use the default Smart logic.
Colors
- Packet color – sets the colors for displaying different kinds of packets (Normal, Bad CRC, Bad ICV) on the Packets tab.
- Colorize Packet Headers – check this box if you want CommView for WiFi to colorize packet contents. If this box is checked, the program displays the first eight packet layers using different colors. To change a color, select the type of header for which you want to change the color and click on the colored rectangle.
- Formula syntax highlighting – sets the colors for highlighting keywords in formulas in the Advanced Rules window.
- Selected byte sequence color – sets the font and background color for displaying the byte sequence that was selected in the decoder tree. For example, when you select the "TCP" tree node, the corresponding part of the packet will be highlighted using these colors.
- Management frame color – sets the colors for different types of Management frames. Color is used in the Protocol column of the Packets tab to show the corresponding frame types.
Decoding
- Always fully expand all nodes in the decoder window – check this box if you would like to have all nodes in the decoder windows automatically expanded when you select a new packet in the packet list.
- Expand the last nodes – check this box if you would like to have the last node(s) in the decoder window automatically expanded when you select a new packet in the packet list and set the number of nodes to be expanded. By default, the first node is expanded. This setting has no effect if the Always fully expand all nodes in the decoder window box is checked.
- Expand level – set the number of levels to expand. This defines the "depth" of tree node expansion.
- Decode up to the first level only in ASCII export – this option affects the decoding format used when you export a packet log or individual packet as an ASCII file with decoding. If this box is checked, only the top-level nodes will be saved. For example, if you save a TCP/IP packet when this option is disabled, all Type of service sub-nodes are saved. When this option is enabled, these sub-nodes are not saved. Checking this box makes the output ASCII file less detailed and more compact.
- Ignore incorrect checksums when reconstructing TCP sessions – this option affects the way CommView for WiFi treats malformed TCP/IP packets when reconstructing TCP sessions. By default, this option is on, and packets with incorrect checksums are not discarded in the process of reconstruction. If you turn off this option, packets with incorrect checksums will be discarded and not displayed in the TCP reconstruction window.
- Include packet numbers when reconstructing TCP sessions – check this box if you'd like the chunks of data shown in the TCP session reconstruction window to be prepended by the packet numbers that correspond to these chunks of data.
- Search for the session start when reconstructing TCP sessions – if this box is checked, the program will attempt to find the beginning of the TCP session when you reconstruct it. If it is not checked, the session will be reconstructed only from the selected packet, i.e. earlier packets will be discarded.
- Decompress GZIP content – check this box if you want CommView for WiFi to convert GZIP-compressed HTTP content into readable text in the TCP Session Reconstruction windows. GZIP content is decompressed only when the display type in the window is set to "ASCII."
- Reconstruct images – check this box if you want CommView for WiFi to convert binary HTTP streams that represent images into viewable JPG, BMP, PNG, and GIF pictures in the TCP Session Reconstruction windows. Images are shown only when the display type in the window is set to "HTML." Images are never shown within the HTML pages to which they belong, as they are transferred by the server in a separate HTTP session.
- Use IPv4-style endings in IPv6 addresses – if this box is not checked, IPv6 addresses are shown using hexadecimal symbols only, e.g. fe80::02c0:26ff:fe2d:edb5. If this box is checked, the last 4 bytes of IPv6 addresses are shown using the IPv4-style dotted notation, e.g. fe80::02c0:26ff:254.45.237.181.
- Reassemble fragmented IP packets – check this box if you would like the program to reassemble IP packets that are fragmented. By default, fragmented IP packets are displayed as they were received from the wire, in their original form. If this option is turned on, the program will maintain an internal buffer of fragments and will attempt to "glue" them, displaying only the results of successful reassembly.
- Display signal level in dBm – check this box if you would like the program to display signal strength in dBm rather than in percentile format. The availability of signal level in dBm depends on the wireless adapter model being used. Please refer to the Understanding Signal Strength chapter for more information.
- Default display type – select the display type value from the drop-down list that you want to set as default for the TCP Session Reconstruction function. The available values are ASCII, HEX, HTML, and EBCDIC.
VoIP
The VoIP analysis module is only available to VoIP license users or evaluation version users who selected VoIP evaluation mode.
- Disable VoIP analysis – disables capture and analysis of VoIP data. Check this box if you do not plan to work with VoIP and want to minimize the usage of computer resources by the application.
- Maximum records in the list – limits the number of displayed and processed VoIP events. When the number of records exceed the specified limit, older records are deleted from the lists.
- Ignore orphan RTP streams – when this box is checked, VoIP analyzer will ignore captured RTP data streams that do not have a parent signaling session. Orphan RTP streams typically appear if packet capturing was started in the middle of a call, or the signaling protocol is unknown to the application (i.e. not SIP and not H.323), or the signaling protocol was sent in a non-standard manner (e.g. encrypted or as part of some other session). Such streams are still available for analysis, and sometimes for playback. Please see the Call Playback chapter for more detailed information on playing VoIP calls. If you are not interested in such orphan streams and want to save on computer resources, please disable this option. Note that when orphan streams are not ignored, VoIP analyzer may mistakenly identify data transferred over UDP protocol as RTP streams. Generally, this is not an error, as RTP packets do not have a standard uniform signature, so such "false positives" are ok.
- Ignore damaged packets in VoIP analyzer – when this box is checked, wireless packets with bad CRC will be discarded by the VoIP analysis module. This prevents the application from creating "ghost" signaling or media streams that may appear if packets with bad CRC are not dropped.
Geolocation
Geolocation is IP-to-country mapping for IP addresses. When this functionality is enabled, CommView for WiFi checks the internal database to provide information on the country any IP address belongs to. You can configure the program to show ISO country code, Country name, or Country flag next to any IP address. You can also disable geolocation. For some IP addresses, such as reserved ones (e.g. 192.168.*.* or 10.*.*.*) no information on the country can be provided. In such cases, the country name is not shown, or if you use the Country flag option, a flag with a question mark is displayed.
As IP allocation is constantly changing, it is important that you always have an up-to-date version of CommView for WiFi. A fresh, up-to-date database is included in every CommView for WiFi build. A fresh database has 98% accuracy. Without updates, the accuracy percentage falls by approximately 15% every year.
Miscellaneous
- Hide from the taskbar on minimization – check this box if you do not want to see the program's button on the Windows taskbar when you minimize the program. If this box is checked, use the program's system tray icon to restore it after minimization.
- Prompt for confirmation when exiting the application – check this box if you would like the program to ask you for a confirmation when you close it.
- Auto-scroll packet data window – if this box is checked, the program scrolls the text of the packet data window automatically when you select a new packet from the packets list (but only if the text does not fit into the window). This is useful when you want to see the contents of a long packet without manually scrolling the window.
- Auto-scroll packet list to the last packet – if this box is checked, the program automatically scrolls the packet list in the Packets tab down to the last received packet.
- Auto-sort new records in the Latest IP Connections – if this box is checked, the program auto-sorts new records on the Latest IP Connections tab based on the user-defined sorting criterion (e.g. ascending order of remote IP addresses).
- Smart CPU utilization control – if this box is checked, the program tries to decrease CPU utilization when capturing high-volume traffic by decreasing the quality and frequency of the screen updates.
- Run on Windows startup - if this box is checked, the program is launched automatically every time you start Windows. Under Windows Vista and higher, this box is disabled if UAC is enabled. This is a limitation of Windows Vista and newer Windows versions that prevent applications with elevated rights from loading on startup. If this feature is important, disable UAC.
- Run minimized – if this box is checked, the program is launched minimized and the main window is not displayed until you click on the tray icon or taskbar button.
- Show gridlines – makes the program draw gridlines in all packet, channel, and AP lists.
- Enable automatic application updates – check this box to let the program connect to the TamoSoft Website periodically and check for updates. Use the Interval between checks box to configure how often the checks should be made.
Plug-ins
- This tab is used by 3rd party plug-ins for performing configuration tasks. Please see Custom Decoding for more information.
Frequently Asked Questions
In this chapter, you can find answers to some of the most frequently asked questions. The latest FAQ is always available at https://www.tamos.com/products/commwifi/faq.php
Q1. I'm on a wireless network, and I want to monitor my own inbound and outbound packets. Which product do I need: the standard, non-wireless CommView edition, or CommView for WiFi?
A. You need the standard, non-wireless CommView edition. It will allow you to monitor your own traffic, but you will not be able to see the traffic of other WLAN stations. Unlike the standard CommView edition, CommView for WiFi allows you to monitor other wireless stations, capture management frames, view signal strength, etc.
Q2.Do I need special hardware to use CommView for WiFi?
A. Yes, you need a compatible wireless adapter. The list of compatible adapters can be found at https://www.tamos.com/products/commwifi/. In order to enable the monitoring features of your wireless adapter, you will need to use the special drivers that come with this product. When CommView for WiFi is not running, your adapter will be able to communicate with other wireless hosts or access points, just like when you are using the original driver supplied by the adapter manufacturer. When CommView for WiFi is running, your adapter will be put in passive, promiscuous monitoring mode.
Q3. My card is not on your list of supported hardware. What are my options?
A. Our hardware compatibility list includes only those cards that we have tested ourselves in our test lab. There are other cards that may be compatible with CommView for WiFi. The best way to find out if your card is compatible is downloading our Adapter Test Utility and running it on your computer. If a compatible adapter is installed, the utility will display its name. Before running our test utility, make sure that you use the latest driver supplied by your computer or adapter vendor. Visit their Website to download and install the latest driver version. This is important, because the results of the test depend on the driver that is used. The newer the driver, the better the chances that it will work with CommView for WiFi. Finally, you may want to buy a compatible card, as they are not terribly expensive these days. Or simply order a boxed version from us; it comes with a compatible USB adapter.
Q4. What adapter would you recommend for use with your application?
A. We suggest that you refer to the list of compatible hardware, which can be found at https://www.tamos.com/products/commwifi/adapterlist.php. By using this list, you choose the best adapter based on the form factor (USB, Integrated, etc.), sensitivity, supported Windows version, and supported 802.11 bands. Generally, the best choice would be an 802.11ac USB adapter.
Q5. Which supported adapters have external antenna connectors?
A. Alfa Networks AWUS1900 and Alfa Networks AWUS036ACM.
Q6. Can I capture data from multiple channels simultaneously?
A. Yes, if you use multiple supported USB adapters. Please refer to the Multi-Channel Capturing chapter for more information.
Q7.I have installed the special driver for my adapter and now the adapter cannot connect to my wireless network after I close CommView for WiFi. What could be the problem?
A. When you replace the driver for your adapter, the configuration settings (including preferred networks and passwords) may be lost, so you may have to re-configure the adapter. If your adapter has been configured and still cannot connect, please disable and re-enable it in Device Manager, this will restore the connectivity.
Q8. Some of the channels are not available in the channel selection controls. Is this normal? What if you want to monitor these channels?
A. The answer depends on the adapter:
- Intel 7xxx, 8xxx, 9xxx, and AX2xx integrated adapters, recommended Realtek-, MediaTek-, and Ralink-based USB adapters, and Atheros-based USB adapters: All channels are always available when using them in CommView for WiFi.
- Atheros-based miniPCI and miniPCIe adapters: Depending on your country, your wireless adapter may not support all the channels shown in that window. The channels that are available for use in a particular country differ according to the regulations of that country. In the United States, for example, FCC regulations only allow channels 1 to 11 to be used in the 2.4 GHz band. The firmware of the wireless adapters being sold in the US is typically configured to disallow channels 12 and 13.
- Other adapters (e.g. Dell or Broadcom): enabling channels 12 and 13 may be possible. Open the CommView for WiFi application folder (usually C:\Program Files (x86)\CommViewWiFi). You will see the file named ch1213.exe there. Double-click on that file to execute it. Restart CommView and these channels will become available for selection. Note that the adapter's ability to capture packets on channels 12 and 13 depends on the regulatory domain set by the laptop vendor. If the vendor enabled them in your case, there won't be a problem. However, we've heard of many examples when laptop vendors did not enable channels 12 and 13 even in the laptops that were sold in a country where these channels were legal.
Q9. When monitoring a WLAN, can I be sure that the program will capture every packet being sent or received?
A. No, and here is why. When a wireless station is connected and authenticated, the station and access point(s) employ a mechanism that allows them to resend the packets that were not received by the other party or damaged en route for some reason (e.g. radio interference). In case of CommView for WiFi, the wireless adapter is put into passive, monitoring mode. Therefore, the adapter cannot send "requests" to have packets resent, nor can it acknowledge successful receipt of packets. This results in loss of some packets. The percentage of lost packets may vary. Generally, the closer to other stations and access points you are, the fewer packets will be dropped.
Q10. Can the program decrypt WPA- and WPA2-encrypted packets?
A. Yes, in WPA-PSK mode. Both TKIP (WPA) and AES/CCMP (WPA2) are supported. WPA3 cannot be decrypted. WPA3 uses the passphrase only for authentication; decryption is impossible.
Q11. I'm on a WLAN with high traffic volume, and it's hard to examine individual packets when the application is receiving hundreds of thousands of packets per second, as the old packets are quickly removed from the circular buffer. Is there anything I can do about it?
A. Yes, you can use the Open current buffer in new window button on the small toolbar on the Packets tab. This will allow you to make snapshots of the current buffer as many times as you wish, at any intervals. You will then be able to explore the packets in these new windows at your leisure.
Q12. I launched the program, selected the channel, started capturing, but no packets are displayed. Please help!
A. First, switch to the Packets tab. The Latest IP Connections tab might be empty if you did not enter correct WEP keys, and your WLAN uses WEP encryption. If the Packets tab is empty too, look at the program's status bar. If the packet counter is being incremented, then you have active rules that prevent the program from displaying packets. Click Rules => Reset All, and then press three toolbar buttons: Capture Data Packets, Capture Management Packets, and Capture Control Packets. If the packet counter on the status bar is not being incremented, then there are probably no active wireless stations or access points available/detected. If you are absolutely certain that there are wireless stations or access points, report this problem to us.
Q13. Can CommView for WiFi read NCF log files generated by the standard, non-wireless CommView edition? How about vice versa?
A. Yes, CommView for WiFi can read NCF log files generated by the standard, non-wireless CommView edition. The standard, non-wireless CommView edition can read NCF log files generated by CommView for WiFi (and will soon be able to read the latest NCFX log format), but you will not be able to see wireless-specific columns, such as signal strength or channel number.
Q14. Does CommView for WiFi run on multi-processor computers?
A. Yes, it does.
Q15. It seems to be impossible to save more than 5,000 packets from the packet buffer. Is there a workaround?
A. Actually, there is no such limitation. The application uses a circular buffer for storing captured packets. By default, the buffer can contain up to 5,000 latest packets, but this value can be adjusted in the Settings window. The maximum buffer size is 20,000 packets (the buffer cannot be unlimited for an obvious reason: your computer’s RAM is not unlimited). You can save the contents of the buffer to a file using the Logging tab. However, by no means does this limit on the buffer size restrict your ability to save any number of packets. You simply need to enable automatic logging on the Logging tab. Such automatic logging will make the application dump all the captured packets to file(s) continuously, and you can set any limit on the total size of the captured data.
Q. My firewall software warns me that CommView for WiFi is "attempting to access the Internet." I am aware that some sites are able to track users by collecting the information sent by their programs via Internet. Why does CommView "attempt to access the Internet"?
A. Three activities may alert your firewall. First, it may be an attempt to resolve IP addresses to hostnames. Since CommView for WiFi has to contact your DNS servers to make a DNS query, it inevitably triggers the alarm. You can disable this feature (Settings => Options => Disable DNS resolving), but in this case, the Latest IP Connections tab will not be able to show you the hostnames. Second, you may have configured the program to check if updates or new versions are available. To do this, CommView for WiFi has to connect to www.tamos.com. You can disable this feature (Settings => Options => Misc. => Enable automatic application updates). Third, when you purchase the product, you need to activate it. If you select online activation, CommView for WiFi has to connect to www.tamos.com. You can avoid this by selecting manual activation. These are the only types of connections CommView for WiFi can potentially make. There are no other hidden activities. We do not sell spyware.
Q17. I'm often logged on as a user without administrative privileges. Do I have to log off and then re-logon as the administrator to be able to run CommView for WiFi?
A. No, you can open CommView for WiFi folder, right-click on the CV.exe file while holding down the Shift key, and select "Run As" from the pop-up menu. Enter the administrative login and password in the window that pops up and click OK to run the program. Under Windows Vista and higher, CommView for WiFi is automatically launched with elevated rights.
Q18. When reconstructing TCP sessions that contain HTML pages in Japanese or Chinese, I cannot see the original text.
A. To see text in East Asian languages, you should install East Asian fonts. Open Control Panel => Regional and Language Options, select the Languages tab, and check the Install files for East Asian languages box.
Q19. I'm confused about the license types available for CommView for WiFi. Could you explain the difference between the license types?
A. Two license types are currently available for CommView for WiFi: Standard license and VoIP license. The more expensive VoIP license enables all the application features, including VoIP analyzer, whereas the standard license does not enable VoIP analyzer.
Additionally, the Standard License is also available as a One Year Subscription, which is a time-limited license valid for one year from the date of purchase only.
CommView for WiFi can also be purchased as a boxed product. Boxed versions include a compatible wireless adapter and a USB flash drive. The price includes UPS ground shipping.
Please refer to the End User License Agreement that comes with the product for other licensing terms and conditions.
Q20. Can I save the audio from the VoIP analyzer to a standard .wav or .mp3 file?
A. Not directly, but there are many utilities on the market that offer a "virtual audio cable" that allows saving anything that is played back through your sound card to a file. Try, for example, Xilisoft Sound Recorder (use the "What you hear" mode).