 |
 |
| |
| Promiscuous Monitoring in Ethernet and Wi-Fi Networks |
|
|||||||||||
|
|
| |
Promiscuous monitoring of Wi-Fi networks has often been a source of confusion, especially among users not professionally involved in wireless software development. It appears logical that if any Ethernet adapter can be used for promiscuous mode monitoring in a wired Ethernet network, then any Wireless Ethernet adapter is equally good for doing the same in a 802.11 a, b, or g network. Theoretically, this is true, but in practice, this is very far from reality. The truth is that the standard drivers for wireless NICs simply don't support promiscuous mode (or, rather, "RF Monitoring", as this feature is called in the wireless world) functionality. While the adapter can receive radio signals on a given frequency regardless of the destination MAC address in the packet, the packets that are not addressed to this adapter are discarded by the driver, and there is no way to make the standard driver pass them to the network monitoring software. The good news is a number of network monitoring software vendors make special RF monitoring drivers for a limited number of supported wireless adapters. Having obtained a supported wireless adapter, the user has to install the wireless monitoring program, replace the original driver by the special RF monitoring driver, and only after that can he monitor the WLAN. Therefore, the frequently asked question, "Does my Wi-Fi card support promiscuous mode?" is, unfortunately, meaningless. This is an issue of driver availability. The correct version of this question would be "Is there a RF monitoring driver for my Wi-Fi card and operating system?" When your wireless network analyzer is up and running, the only thing required for monitoring a WLAN is being within the signal range. Then the software can intercept and display wireless packets, show nodes and access points, signal strength, and other important statistics and indicators. 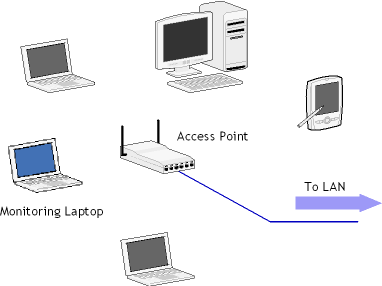
A typical wireless monitoring layout is simple: Just a number of computers and access points and a computer running a network analyzer in the vicinity. Your network analyzer would display your WLAN nodes in a way similar to the one shown in the screen shot below: 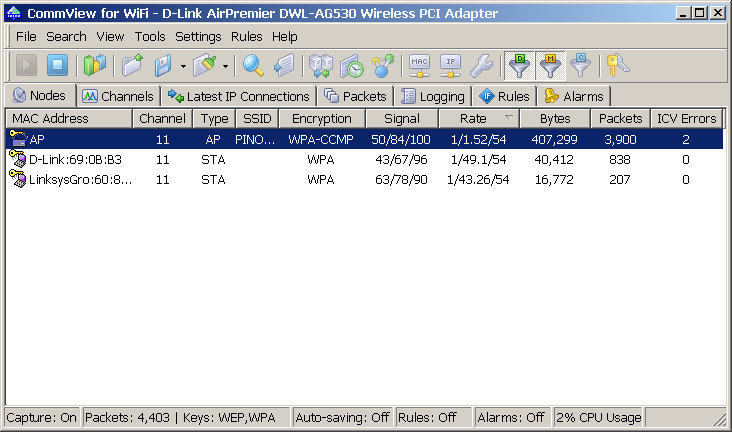
Aside from the problems related to NIC drivers, wireless traffic is sometimes encrypted using WEP (an older standard) or WPA. A good WLAN analyzer must be capable of decrypting encrypted network traffic on the fly utilizing a user-provided WEP or WPA-PSK key. A WLAN analyzer may not be required if all you need to monitor is the traffic between the wireless stations and the Internet. Using a standard, non-wireless monitor on a mirror port would make it possible to capture the packets being sent and received through the access point. A network layout illustrating this method is shown below. 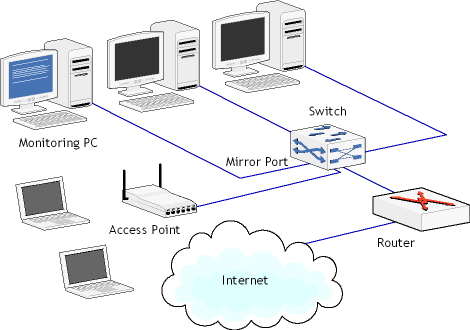
Naturally, this setup can't be used to see the traffic between the wireless stations or gain access to wireless-specific indicators and data, such as signal strength, data transfer rate, or intrusion incidents. |
|||||||||